cloudsplaining-0.1.6/�������������������������������������������������������������������������������0000755�0001751�0000164�00000000000�13702127551�015335� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/MANIFEST.in��������������������������������������������������������������������0000644�0001751�0000164�00000000212�13702127516�017067� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������recursive-include cloudsplaining/shared *.yml
recursive-include cloudsplaining/output *.html
recursive-include cloudsplaining/output *.md
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/PKG-INFO�����������������������������������������������������������������������0000644�0001751�0000164�00000046274�13702127551�016447� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������Metadata-Version: 2.1
Name: cloudsplaining
Version: 0.1.6
Summary: AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report with a triage worksheet.
Home-page: https://github.com/kmcquade/cloudsplaining
Author: Kinnaird McQuade
Author-email: kinnairdm@gmail.com
License: UNKNOWN
Description: Cloudsplaining
--------------
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report.

[](https://cloudsplaining.readthedocs.io/en/latest/?badge=latest)
[](https://gitter.im/cloudsplaining?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge&utm_content=badge)
[](https://pepy.tech/project/cloudsplaining)
* [Example report](https://opensource.salesforce.com/cloudsplaining/)
> 
## Documentation
For full documentation, please visit the [project on ReadTheDocs](https://cloudsplaining.readthedocs.io/en/latest/).
* [Installation](#installation)
* [Cheat sheet](#cheatsheet)
* [Example report](https://opensource.salesforce.com/cloudsplaining/)
## Overview
Cloudsplaining identifies violations of least privilege in AWS IAM policies and generates a pretty HTML report with a triage worksheet. It can scan all the policies in your AWS account or it can scan a single policy file.
It helps to identify IAM actions that do not leverage resource constraints. It also helps prioritize the remediation process by flagging IAM policies that present the following risks to the AWS account in question without restriction:
* Data Exfiltration (`s3:GetObject`, `ssm:GetParameter`, `secretsmanager:GetSecretValue`)
* Infrastructure Modification
* Resource Exposure (the ability to modify resource-based policies)
* Privilege Escalation (based on Rhino Security Labs research)
Cloudsplaining also identifies IAM Roles that can be assumed by AWS Compute Services (such as EC2, ECS, EKS, or Lambda), as they can present greater risk than user-defined roles - especially if the AWS Compute service is on an instance that is directly or indirectly exposed to the internet. Flagging these roles is particularly useful to penetration testers (or attackers) under certain scenarios. For example, if an attacker obtains privileges to execute [ssm:SendCommand](https://docs.aws.amazon.com/systems-manager/latest/APIReference/API_SendCommand.html) and there are privileged EC2 instances with the SSM agent installed, they can effectively have the privileges of those EC2 instances. Remote Code Execution via AWS Systems Manager Agent was already a known escalation/exploitation path, but Cloudsplaining can make the process of identifying theses cases easier. See the [sample report](https://opensource.salesforce.com/cloudsplaining/#executive-summary) for some examples.
You can also specify a custom exclusions file to filter out results that are False Positives for various reasons. For example, User Policies are permissive by design, whereas System roles are generally more restrictive. You might also have exclusions that are specific to your organization's multi-account strategy or AWS application architecture.
## Motivation
[Policy Sentry](https://engineering.salesforce.com/salesforce-cloud-security-automating-least-privilege-in-aws-iam-with-policy-sentry-b04fe457b8dc) revealed to us that it is possible to finally write IAM policies according to least privilege in a scalable manner. Before Policy Sentry was released, it was too easy to find IAM policy documents that lacked resource constraints. Consider the policy below, which allows the IAM principal (a role or user) to run `s3:PutObject` on any S3 bucket in the AWS account:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:PutObject"
],
"Resource": "*"
}
]
}
```
This is bad. Ideally, access should be restricted according to resource ARNs, like so:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": "arn:aws:s3:::my-bucket/*"
}
]
}
```
Policy Sentry [makes it really easy to do this](https://github.com/salesforce/policy_sentry/#policy-sentry). Once Infrastructure as Code developers or AWS Administrators gain familiarity with the tool (which is quite easy to use), we've found that adoption starts very quickly. **However**, if you've been using AWS, there is probably a very large backlog of IAM policies that could use an uplift. If you have hundreds of AWS accounts with dozens of policies in each, how can we lock down those AWS accounts by programmatically identifying the policies that should be fixed?
That's why we wrote Cloudsplaining.
Cloudsplaining identifies violations of least privilege in AWS IAM policies and generates a pretty HTML report with a triage worksheet. It can scan all the policies in your AWS account or it can scan a single policy file.
## Installation
* Homebrew
```bash
brew tap salesforce/cloudsplaining https://github.com/salesforce/cloudsplaining
brew install cloudsplaining
```
* Pip3
```bash
pip3 install --user cloudsplaining
```
* Now you should be able to execute `cloudsplaining` from command line by running `cloudsplaining --help`.
### Scanning an entire AWS Account
#### Downloading Account Authorization Details
We can scan an entire AWS account and generate reports. To do this, we leverage the AWS IAM [get-account-authorization-details](https://docs.aws.amazon.com/cli/latest/reference/iam/get-account-authorization-details.html) API call, which downloads a large JSON file (around 100KB per account) that contains all of the IAM details for the account. This includes data on users, groups, roles, customer-managed policies, and AWS-managed policies.
* You must have AWS credentials configured that can be used by the CLI.
* You must have the privileges to run [iam:GetAccountAuthorizationDetails](https://docs.aws.amazon.com/IAM/latest/APIReference/API_GetAccountAuthorizationDetails.html). The `arn:aws:iam::aws:policy/SecurityAudit` policy includes this, as do many others that allow Read access to the IAM Service.
* To download the account authorization details, ensure you are authenticated to AWS, then run `cloudsplaining`'s `download` command:
```bash
cloudsplaining download
```
* If you prefer to use your `~/.aws/credentials` file instead of environment variables, you can specify the profile name:
```bash
cloudsplaining download --profile myprofile
```
It will download a JSON file in your current directory that contains your account authorization detail information.
#### Create Exclusions file
Cloudsplaining tool does not attempt to understand the context behind everything in your AWS account. It's possible to understand the context behind some of these things programmatically - whether the policy is applied to an instance profile, whether the policy is attached, whether inline IAM policies are in use, and whether or not AWS Managed Policies are in use. **Only you know the context behind the design of your AWS infrastructure and the IAM strategy**.
As such, it's important to eliminate False Positives that are context-dependent. You can do this with an exclusions file. We've included a command that will generate an exclusions file for you so you don't have to remember the required format.
You can create an exclusions template via the following command:
```bash
cloudsplaining create-exclusions-file
```
This will generate a file in your current directory titled `exclusions.yml`.
Now when you run the `scan` command, you can use the exclusions file like this:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
For more information on the structure of the exclusions file, see [Filtering False Positives](#filtering-false-positives)
#### Scanning the Authorization Details file
Now that we've downloaded the account authorization file, we can scan *all* of the AWS IAM policies with `cloudsplaining`.
Run the following command:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
It will create an HTML report like [this](https://opensource.salesforce.com/cloudsplaining/):
> 
It will also create a raw JSON data file:
* `default-iam-results.json`: This contains the raw JSON output of the report. You can use this data file for operating on the scan results for various purposes. For example, you could write a Python script that parses this data and opens up automated JIRA issues or Salesforce Work Items. An example entry is shown below. The full example can be viewed at [examples/output/example-authz-details-results.json](examples/files/iam-results-example.json)
```json
{
"example-authz-details": [
{
"AccountID": "012345678901",
"ManagedBy": "Customer",
"PolicyName": "InsecureUserPolicy",
"Arn": "arn:aws:iam::012345678901:user/userwithlotsofpermissions",
"ActionsCount": 2,
"ServicesCount": 1,
"Actions": [
"s3:PutObject",
"s3:PutObjectAcl"
],
"Services": [
"s3"
]
}
]
}
```
See the [examples/files](examples/files) folder for sample output.
#### Filtering False Positives
Resource constraints are best practice - especially for system roles/instance profiles - but sometimes, these are by design. For example, consider a situation where a custom IAM policy is used on an instance profile for an EC2 instance that provisions Terraform. *In this case, broad permissions are design requirements* - so we don't want to include these in the results.
You can create an exclusions template via the following command:
```bash
cloudsplaining create-exclusions-file
```
This will generate a file in your current directory titled `exclusions.yml`.
The default exclusions file looks like this:
```yaml
# Policy names to exclude from evaluation
# Suggestion: Add policies here that are known to be overly permissive by design, after you run the initial report.
policies:
- "AWSServiceRoleFor*"
- "*ServiceRolePolicy"
- "*ServiceLinkedRolePolicy"
- "AdministratorAccess" # Otherwise, this will take a long time
- "service-role*"
- "aws-service-role*"
# Don't evaluate these roles, users, or groups as part of the evaluation
roles:
- "service-role*"
- "aws-service-role*"
users:
- ""
groups:
- ""
# Read-only actions to include in the results, such as s3:GetObject
# By default, it includes Actions that could lead to Data Leaks
include-actions:
- "s3:GetObject"
- "ssm:GetParameter"
- "ssm:GetParameters"
- "ssm:GetParametersByPath"
- "secretsmanager:GetSecretValue"
# Write actions to include from the results, such as kms:Decrypt
exclude-actions:
- ""
```
* Make any additions or modifications that you want.
* Under `policies`, list the path of policy names that you want to exclude.
* If you want to exclude a role titled `MyRole`, list `MyRole` or `MyR*` in the `roles` list.
* You can follow the same approach for `users` and `groups` list.
Now when you run the `scan` command, you can use the exclusions file like this:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
### Scanning a single policy
You can also scan a single policy file to identify risks instead of an entire account.
```bash
cloudsplaining scan-policy-file --input examples/policies/explicit-actions.json
```
The output will include a finding description and a list of the IAM actions that do not leverage resource constraints.
The output will resemble the following:
```console
Issue found: Data Exfiltration
Actions: s3:GetObject
Issue found: Resource Exposure
Actions: ecr:DeleteRepositoryPolicy, ecr:SetRepositoryPolicy, s3:BypassGovernanceRetention, s3:DeleteAccessPointPolicy, s3:DeleteBucketPolicy, s3:ObjectOwnerOverrideToBucketOwner, s3:PutAccessPointPolicy, s3:PutAccountPublicAccessBlock, s3:PutBucketAcl, s3:PutBucketPolicy, s3:PutBucketPublicAccessBlock, s3:PutObjectAcl, s3:PutObjectVersionAcl
Issue found: Unrestricted Infrastructure Modification
Actions: ecr:BatchDeleteImage, ecr:CompleteLayerUpload, ecr:CreateRepository, ecr:DeleteLifecyclePolicy, ecr:DeleteRepository, ecr:DeleteRepositoryPolicy, ecr:InitiateLayerUpload, ecr:PutImage, ecr:PutImageScanningConfiguration, ecr:PutImageTagMutability, ecr:PutLifecyclePolicy, ecr:SetRepositoryPolicy, ecr:StartImageScan, ecr:StartLifecyclePolicyPreview, ecr:TagResource, ecr:UntagResource, ecr:UploadLayerPart, s3:AbortMultipartUpload, s3:BypassGovernanceRetention, s3:CreateAccessPoint, s3:CreateBucket, s3:DeleteAccessPoint, s3:DeleteAccessPointPolicy, s3:DeleteBucket, s3:DeleteBucketPolicy, s3:DeleteBucketWebsite, s3:DeleteObject, s3:DeleteObjectTagging, s3:DeleteObjectVersion, s3:DeleteObjectVersionTagging, s3:GetObject, s3:ObjectOwnerOverrideToBucketOwner, s3:PutAccelerateConfiguration, s3:PutAccessPointPolicy, s3:PutAnalyticsConfiguration, s3:PutBucketAcl, s3:PutBucketCORS, s3:PutBucketLogging, s3:PutBucketNotification, s3:PutBucketObjectLockConfiguration, s3:PutBucketPolicy, s3:PutBucketPublicAccessBlock, s3:PutBucketRequestPayment, s3:PutBucketTagging, s3:PutBucketVersioning, s3:PutBucketWebsite, s3:PutEncryptionConfiguration, s3:PutInventoryConfiguration, s3:PutLifecycleConfiguration, s3:PutMetricsConfiguration, s3:PutObject, s3:PutObjectAcl, s3:PutObjectLegalHold, s3:PutObjectRetention, s3:PutObjectTagging, s3:PutObjectVersionAcl, s3:PutObjectVersionTagging, s3:PutReplicationConfiguration, s3:ReplicateDelete, s3:ReplicateObject, s3:ReplicateTags, s3:RestoreObject, s3:UpdateJobPriority, s3:UpdateJobStatus
```
## Cheatsheet
```bash
# Download authorization details
cloudsplaining download
# Download from a specific profile
cloudsplaining download --profile someprofile
# Scan Authorization details
cloudsplaining scan --input default.json
# Scan Authorization details with custom exclusions
cloudsplaining scan --input default.json --exclusions-file exclusions.yml
# Scan Policy Files
cloudsplaining scan-policy-file --input examples/policies/wildcards.json
cloudsplaining scan-policy-file --input examples/policies/wildcards.json --exclusions-file examples/example-exclusions.yml
```
## FAQ
**Will it scan all policies by default?**
No, it will only scan policies that are attached to IAM principals.
**Will the download command download all policy versions?**
Not by default. If you want to do this, specify the `--include-non-default-policy-versions` flag. Note that the `scan` tool does not currently operate on non-default versions.
**I followed the installation instructions but can't execute the program via command line at all. What do I do?**
This is likely an issue with your PATH. Your PATH environment variable is not considering the binary packages installed by `pip3`. On a Mac, you can likely fix this by entering the command below, depending on the versions you have installed. YMMV.
```bash
export PATH=$HOME/Library/Python/3.7/bin/:$PATH
```
**I followed the installation instructions but I am receiving a `ModuleNotFoundError` that says `No module named policy_sentry.analysis.expand`. What should I do?**
Try upgrading to the latest version of Cloudsplaining. This error was fixed in version 0.0.10.
## References
* [Policy Sentry](https://github.com/salesforce/policy_sentry/) by [Kinnaird McQuade](https://twitter.com/kmcquade3) at Salesforce
* [Parliament](https://github.com/duo-labs/parliament/) by [Scott Piper](https://twitter.com/0xdabbad00) at [Summit Route](http://summitroute.com/) and Duo Labs.
* [AWS Privilege Escalation Methods](https://github.com/RhinoSecurityLabs/AWS-IAM-Privilege-Escalation) by [Spencer Gietzen](https://twitter.com/SpenGietz) at Rhino Security Labs
* [Understanding Access Level Summaries within Policy Summaries](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_understand-policy-summary-access-level-summaries.html)
* [Leveraging next-generation blockchain-based AI across multiple service meshes to transparently automate multi-cloud IAM wizardry :mage_man:](http://kmcquade.com/rick.html)
Keywords: aws iam roles policy policies privileges security
Platform: UNKNOWN
Classifier: Programming Language :: Python :: 3
Classifier: License :: OSI Approved :: MIT License
Classifier: Operating System :: OS Independent
Requires-Python: >=3.6
Description-Content-Type: text/markdown
������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/README.md����������������������������������������������������������������������0000644�0001751�0000164�00000040125�13702127516�016617� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������Cloudsplaining
--------------
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report.

[](https://cloudsplaining.readthedocs.io/en/latest/?badge=latest)
[](https://gitter.im/cloudsplaining?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge&utm_content=badge)
[](https://pepy.tech/project/cloudsplaining)
* [Example report](https://opensource.salesforce.com/cloudsplaining/)
> 
## Documentation
For full documentation, please visit the [project on ReadTheDocs](https://cloudsplaining.readthedocs.io/en/latest/).
* [Installation](#installation)
* [Cheat sheet](#cheatsheet)
* [Example report](https://opensource.salesforce.com/cloudsplaining/)
## Overview
Cloudsplaining identifies violations of least privilege in AWS IAM policies and generates a pretty HTML report with a triage worksheet. It can scan all the policies in your AWS account or it can scan a single policy file.
It helps to identify IAM actions that do not leverage resource constraints. It also helps prioritize the remediation process by flagging IAM policies that present the following risks to the AWS account in question without restriction:
* Data Exfiltration (`s3:GetObject`, `ssm:GetParameter`, `secretsmanager:GetSecretValue`)
* Infrastructure Modification
* Resource Exposure (the ability to modify resource-based policies)
* Privilege Escalation (based on Rhino Security Labs research)
Cloudsplaining also identifies IAM Roles that can be assumed by AWS Compute Services (such as EC2, ECS, EKS, or Lambda), as they can present greater risk than user-defined roles - especially if the AWS Compute service is on an instance that is directly or indirectly exposed to the internet. Flagging these roles is particularly useful to penetration testers (or attackers) under certain scenarios. For example, if an attacker obtains privileges to execute [ssm:SendCommand](https://docs.aws.amazon.com/systems-manager/latest/APIReference/API_SendCommand.html) and there are privileged EC2 instances with the SSM agent installed, they can effectively have the privileges of those EC2 instances. Remote Code Execution via AWS Systems Manager Agent was already a known escalation/exploitation path, but Cloudsplaining can make the process of identifying theses cases easier. See the [sample report](https://opensource.salesforce.com/cloudsplaining/#executive-summary) for some examples.
You can also specify a custom exclusions file to filter out results that are False Positives for various reasons. For example, User Policies are permissive by design, whereas System roles are generally more restrictive. You might also have exclusions that are specific to your organization's multi-account strategy or AWS application architecture.
## Motivation
[Policy Sentry](https://engineering.salesforce.com/salesforce-cloud-security-automating-least-privilege-in-aws-iam-with-policy-sentry-b04fe457b8dc) revealed to us that it is possible to finally write IAM policies according to least privilege in a scalable manner. Before Policy Sentry was released, it was too easy to find IAM policy documents that lacked resource constraints. Consider the policy below, which allows the IAM principal (a role or user) to run `s3:PutObject` on any S3 bucket in the AWS account:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:PutObject"
],
"Resource": "*"
}
]
}
```
This is bad. Ideally, access should be restricted according to resource ARNs, like so:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": "arn:aws:s3:::my-bucket/*"
}
]
}
```
Policy Sentry [makes it really easy to do this](https://github.com/salesforce/policy_sentry/#policy-sentry). Once Infrastructure as Code developers or AWS Administrators gain familiarity with the tool (which is quite easy to use), we've found that adoption starts very quickly. **However**, if you've been using AWS, there is probably a very large backlog of IAM policies that could use an uplift. If you have hundreds of AWS accounts with dozens of policies in each, how can we lock down those AWS accounts by programmatically identifying the policies that should be fixed?
That's why we wrote Cloudsplaining.
Cloudsplaining identifies violations of least privilege in AWS IAM policies and generates a pretty HTML report with a triage worksheet. It can scan all the policies in your AWS account or it can scan a single policy file.
## Installation
* Homebrew
```bash
brew tap salesforce/cloudsplaining https://github.com/salesforce/cloudsplaining
brew install cloudsplaining
```
* Pip3
```bash
pip3 install --user cloudsplaining
```
* Now you should be able to execute `cloudsplaining` from command line by running `cloudsplaining --help`.
### Scanning an entire AWS Account
#### Downloading Account Authorization Details
We can scan an entire AWS account and generate reports. To do this, we leverage the AWS IAM [get-account-authorization-details](https://docs.aws.amazon.com/cli/latest/reference/iam/get-account-authorization-details.html) API call, which downloads a large JSON file (around 100KB per account) that contains all of the IAM details for the account. This includes data on users, groups, roles, customer-managed policies, and AWS-managed policies.
* You must have AWS credentials configured that can be used by the CLI.
* You must have the privileges to run [iam:GetAccountAuthorizationDetails](https://docs.aws.amazon.com/IAM/latest/APIReference/API_GetAccountAuthorizationDetails.html). The `arn:aws:iam::aws:policy/SecurityAudit` policy includes this, as do many others that allow Read access to the IAM Service.
* To download the account authorization details, ensure you are authenticated to AWS, then run `cloudsplaining`'s `download` command:
```bash
cloudsplaining download
```
* If you prefer to use your `~/.aws/credentials` file instead of environment variables, you can specify the profile name:
```bash
cloudsplaining download --profile myprofile
```
It will download a JSON file in your current directory that contains your account authorization detail information.
#### Create Exclusions file
Cloudsplaining tool does not attempt to understand the context behind everything in your AWS account. It's possible to understand the context behind some of these things programmatically - whether the policy is applied to an instance profile, whether the policy is attached, whether inline IAM policies are in use, and whether or not AWS Managed Policies are in use. **Only you know the context behind the design of your AWS infrastructure and the IAM strategy**.
As such, it's important to eliminate False Positives that are context-dependent. You can do this with an exclusions file. We've included a command that will generate an exclusions file for you so you don't have to remember the required format.
You can create an exclusions template via the following command:
```bash
cloudsplaining create-exclusions-file
```
This will generate a file in your current directory titled `exclusions.yml`.
Now when you run the `scan` command, you can use the exclusions file like this:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
For more information on the structure of the exclusions file, see [Filtering False Positives](#filtering-false-positives)
#### Scanning the Authorization Details file
Now that we've downloaded the account authorization file, we can scan *all* of the AWS IAM policies with `cloudsplaining`.
Run the following command:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
It will create an HTML report like [this](https://opensource.salesforce.com/cloudsplaining/):
> 
It will also create a raw JSON data file:
* `default-iam-results.json`: This contains the raw JSON output of the report. You can use this data file for operating on the scan results for various purposes. For example, you could write a Python script that parses this data and opens up automated JIRA issues or Salesforce Work Items. An example entry is shown below. The full example can be viewed at [examples/output/example-authz-details-results.json](examples/files/iam-results-example.json)
```json
{
"example-authz-details": [
{
"AccountID": "012345678901",
"ManagedBy": "Customer",
"PolicyName": "InsecureUserPolicy",
"Arn": "arn:aws:iam::012345678901:user/userwithlotsofpermissions",
"ActionsCount": 2,
"ServicesCount": 1,
"Actions": [
"s3:PutObject",
"s3:PutObjectAcl"
],
"Services": [
"s3"
]
}
]
}
```
See the [examples/files](examples/files) folder for sample output.
#### Filtering False Positives
Resource constraints are best practice - especially for system roles/instance profiles - but sometimes, these are by design. For example, consider a situation where a custom IAM policy is used on an instance profile for an EC2 instance that provisions Terraform. *In this case, broad permissions are design requirements* - so we don't want to include these in the results.
You can create an exclusions template via the following command:
```bash
cloudsplaining create-exclusions-file
```
This will generate a file in your current directory titled `exclusions.yml`.
The default exclusions file looks like this:
```yaml
# Policy names to exclude from evaluation
# Suggestion: Add policies here that are known to be overly permissive by design, after you run the initial report.
policies:
- "AWSServiceRoleFor*"
- "*ServiceRolePolicy"
- "*ServiceLinkedRolePolicy"
- "AdministratorAccess" # Otherwise, this will take a long time
- "service-role*"
- "aws-service-role*"
# Don't evaluate these roles, users, or groups as part of the evaluation
roles:
- "service-role*"
- "aws-service-role*"
users:
- ""
groups:
- ""
# Read-only actions to include in the results, such as s3:GetObject
# By default, it includes Actions that could lead to Data Leaks
include-actions:
- "s3:GetObject"
- "ssm:GetParameter"
- "ssm:GetParameters"
- "ssm:GetParametersByPath"
- "secretsmanager:GetSecretValue"
# Write actions to include from the results, such as kms:Decrypt
exclude-actions:
- ""
```
* Make any additions or modifications that you want.
* Under `policies`, list the path of policy names that you want to exclude.
* If you want to exclude a role titled `MyRole`, list `MyRole` or `MyR*` in the `roles` list.
* You can follow the same approach for `users` and `groups` list.
Now when you run the `scan` command, you can use the exclusions file like this:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
### Scanning a single policy
You can also scan a single policy file to identify risks instead of an entire account.
```bash
cloudsplaining scan-policy-file --input examples/policies/explicit-actions.json
```
The output will include a finding description and a list of the IAM actions that do not leverage resource constraints.
The output will resemble the following:
```console
Issue found: Data Exfiltration
Actions: s3:GetObject
Issue found: Resource Exposure
Actions: ecr:DeleteRepositoryPolicy, ecr:SetRepositoryPolicy, s3:BypassGovernanceRetention, s3:DeleteAccessPointPolicy, s3:DeleteBucketPolicy, s3:ObjectOwnerOverrideToBucketOwner, s3:PutAccessPointPolicy, s3:PutAccountPublicAccessBlock, s3:PutBucketAcl, s3:PutBucketPolicy, s3:PutBucketPublicAccessBlock, s3:PutObjectAcl, s3:PutObjectVersionAcl
Issue found: Unrestricted Infrastructure Modification
Actions: ecr:BatchDeleteImage, ecr:CompleteLayerUpload, ecr:CreateRepository, ecr:DeleteLifecyclePolicy, ecr:DeleteRepository, ecr:DeleteRepositoryPolicy, ecr:InitiateLayerUpload, ecr:PutImage, ecr:PutImageScanningConfiguration, ecr:PutImageTagMutability, ecr:PutLifecyclePolicy, ecr:SetRepositoryPolicy, ecr:StartImageScan, ecr:StartLifecyclePolicyPreview, ecr:TagResource, ecr:UntagResource, ecr:UploadLayerPart, s3:AbortMultipartUpload, s3:BypassGovernanceRetention, s3:CreateAccessPoint, s3:CreateBucket, s3:DeleteAccessPoint, s3:DeleteAccessPointPolicy, s3:DeleteBucket, s3:DeleteBucketPolicy, s3:DeleteBucketWebsite, s3:DeleteObject, s3:DeleteObjectTagging, s3:DeleteObjectVersion, s3:DeleteObjectVersionTagging, s3:GetObject, s3:ObjectOwnerOverrideToBucketOwner, s3:PutAccelerateConfiguration, s3:PutAccessPointPolicy, s3:PutAnalyticsConfiguration, s3:PutBucketAcl, s3:PutBucketCORS, s3:PutBucketLogging, s3:PutBucketNotification, s3:PutBucketObjectLockConfiguration, s3:PutBucketPolicy, s3:PutBucketPublicAccessBlock, s3:PutBucketRequestPayment, s3:PutBucketTagging, s3:PutBucketVersioning, s3:PutBucketWebsite, s3:PutEncryptionConfiguration, s3:PutInventoryConfiguration, s3:PutLifecycleConfiguration, s3:PutMetricsConfiguration, s3:PutObject, s3:PutObjectAcl, s3:PutObjectLegalHold, s3:PutObjectRetention, s3:PutObjectTagging, s3:PutObjectVersionAcl, s3:PutObjectVersionTagging, s3:PutReplicationConfiguration, s3:ReplicateDelete, s3:ReplicateObject, s3:ReplicateTags, s3:RestoreObject, s3:UpdateJobPriority, s3:UpdateJobStatus
```
## Cheatsheet
```bash
# Download authorization details
cloudsplaining download
# Download from a specific profile
cloudsplaining download --profile someprofile
# Scan Authorization details
cloudsplaining scan --input default.json
# Scan Authorization details with custom exclusions
cloudsplaining scan --input default.json --exclusions-file exclusions.yml
# Scan Policy Files
cloudsplaining scan-policy-file --input examples/policies/wildcards.json
cloudsplaining scan-policy-file --input examples/policies/wildcards.json --exclusions-file examples/example-exclusions.yml
```
## FAQ
**Will it scan all policies by default?**
No, it will only scan policies that are attached to IAM principals.
**Will the download command download all policy versions?**
Not by default. If you want to do this, specify the `--include-non-default-policy-versions` flag. Note that the `scan` tool does not currently operate on non-default versions.
**I followed the installation instructions but can't execute the program via command line at all. What do I do?**
This is likely an issue with your PATH. Your PATH environment variable is not considering the binary packages installed by `pip3`. On a Mac, you can likely fix this by entering the command below, depending on the versions you have installed. YMMV.
```bash
export PATH=$HOME/Library/Python/3.7/bin/:$PATH
```
**I followed the installation instructions but I am receiving a `ModuleNotFoundError` that says `No module named policy_sentry.analysis.expand`. What should I do?**
Try upgrading to the latest version of Cloudsplaining. This error was fixed in version 0.0.10.
## References
* [Policy Sentry](https://github.com/salesforce/policy_sentry/) by [Kinnaird McQuade](https://twitter.com/kmcquade3) at Salesforce
* [Parliament](https://github.com/duo-labs/parliament/) by [Scott Piper](https://twitter.com/0xdabbad00) at [Summit Route](http://summitroute.com/) and Duo Labs.
* [AWS Privilege Escalation Methods](https://github.com/RhinoSecurityLabs/AWS-IAM-Privilege-Escalation) by [Spencer Gietzen](https://twitter.com/SpenGietz) at Rhino Security Labs
* [Understanding Access Level Summaries within Policy Summaries](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_understand-policy-summary-access-level-summaries.html)
* [Leveraging next-generation blockchain-based AI across multiple service meshes to transparently automate multi-cloud IAM wizardry :mage_man:](http://kmcquade.com/rick.html)
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/����������������������������������������������������������������0000755�0001751�0000164�00000000000�13702127550�020347� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/__init__.py�����������������������������������������������������0000644�0001751�0000164�00000000416�13702127516�022463� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# pylint: disable=missing-module-docstring
import logging
# Set default logging handler to avoid "No handler found" warnings.
from logging import NullHandler
logging.getLogger(__name__).addHandler(NullHandler())
name = "cloudsplaining" # pylint: disable=invalid-name
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/bin/������������������������������������������������������������0000755�0001751�0000164�00000000000�13702127550�021117� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/bin/__init__.py�������������������������������������������������0000644�0001751�0000164�00000000000�13702127516�023220� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/bin/cli.py������������������������������������������������������0000755�0001751�0000164�00000002512�13702127516�022245� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������#! /usr/bin/env python
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
"""
Cloudsplaining is an AWS IAM Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report with a triage worksheet.
"""
import click
from cloudsplaining import command
from cloudsplaining.bin.version import __version__
@click.group()
@click.version_option(version=__version__)
def cloudsplaining():
"""
Cloudsplaining is an AWS IAM Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report with a triage worksheet.
"""
cloudsplaining.add_command(command.create_exclusions_file.create_exclusions_file)
cloudsplaining.add_command(command.expand_policy.expand_policy)
cloudsplaining.add_command(command.scan.scan)
cloudsplaining.add_command(command.scan_policy_file.scan_policy_file)
cloudsplaining.add_command(command.download.download)
def main():
"""Cloudsplaining is an AWS IAM Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report with a triage worksheet."""
cloudsplaining()
if __name__ == "__main__":
cloudsplaining()
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/bin/version.py��������������������������������������������������0000644�0001751�0000164�00000000101�13702127516�023150� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# pylint: disable=missing-module-docstring
__version__ = "0.1.6"
���������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/command/��������������������������������������������������������0000755�0001751�0000164�00000000000�13702127550�021765� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/command/__init__.py���������������������������������������������0000644�0001751�0000164�00000000436�13702127516�024103� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# pylint: disable=missing-module-docstring
from cloudsplaining.command import create_exclusions_file
from cloudsplaining.command import expand_policy
from cloudsplaining.command import download
from cloudsplaining.command import scan
from cloudsplaining.command import scan_policy_file
����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/command/create_exclusions_file.py�������������������������������0000644�0001751�0000164�00000003465�13702127516�027067� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""
Create YML Template files for the exclusions template command.
This way, users don't have to remember exactly how to phrase the yaml files, since this command creates it for them.
"""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import os
from pathlib import Path
import logging
import click
import click_log
from cloudsplaining.shared.constants import EXCLUSIONS_TEMPLATE
logger = logging.getLogger()
click_log.basic_config(logger)
@click.command(
context_settings=dict(max_content_width=160),
short_help="Creates a YML file to be used as a custom exclusions template",
)
@click.option(
"--output-file",
type=click.Path(exists=False),
default=os.path.join(os.getcwd(), "exclusions.yml"),
required=True,
help="Relative path to output file where we want to store the exclusions template.",
)
@click_log.simple_verbosity_option(logger)
def create_exclusions_file(output_file):
"""
Creates a YML file to be used as a custom exclusions template,
so users can fill out the fields without needing to look up the required format.
"""
filename = Path(output_file).resolve()
with open(filename, "a") as file_obj:
for line in EXCLUSIONS_TEMPLATE:
file_obj.write(line)
print(f"Exclusions template file written to: {filename}")
print(
"Make sure you download your account authorization details before running the scan. Set your AWS access keys as environment variables then run: "
)
print("\tcloudsplaining download")
print("You can use this with the scan command as shown below: ")
print("\tcloudsplaining scan --exclusions-file exclusions.yml --input default.json")
�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/command/download.py���������������������������������������������0000644�0001751�0000164�00000012346�13702127516�024156� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Runs aws iam get-authorization-details on all accounts specified in the aws credentials file, and stores them in
account-alias.json """
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import os
import json
import logging
from pathlib import Path
import boto3
import click
import click_log
from botocore.config import Config
logger = logging.getLogger()
click_log.basic_config(logger)
@click.command(
short_help="Runs aws iam get-authorization-details on all accounts specified in the aws credentials "
"file, and stores them in account-alias.json"
)
@click.option(
"--profile",
type=str,
required=False,
help="Specify 'all' to authenticate to AWS and analyze *all* existing IAM policies. Specify a non-default "
"profile here. Defaults to the 'default' profile.",
)
@click.option(
"--output",
type=click.Path(exists=True),
default=Path.cwd(),
help="Path to store the output. Defaults to current directory.",
)
@click.option(
"--include-non-default-policy-versions",
is_flag=True,
default=False,
help="When downloading AWS managed policy documents, also include the non-default policy versions."
" Note that this will dramatically increase the size of the downloaded file.",
)
@click_log.simple_verbosity_option(logger)
def download(profile, output, include_non_default_policy_versions):
"""
Runs aws iam get-authorization-details on all accounts specified in the aws credentials file, and stores them in
account-alias.json
"""
default_region = "us-east-1"
session_data = {"region_name": default_region}
if profile:
session_data["profile_name"] = profile
output_filename = os.path.join(output, f"{profile}.json")
else:
output_filename = "default.json"
results = get_account_authorization_details(session_data, include_non_default_policy_versions)
if os.path.exists(output_filename):
os.remove(output_filename)
with open(output_filename, "w") as file:
json.dump(results, file, indent=4, default=str)
print(f"Saved results to {output_filename}")
return 1
def get_account_authorization_details(session_data, include_non_default_policy_versions):
"""Runs aws-iam-get-account-authorization-details"""
session = boto3.Session(**session_data)
config = Config(connect_timeout=5, retries={"max_attempts": 10})
iam_client = session.client("iam", config=config)
results = {
"UserDetailList": [],
"GroupDetailList": [],
"RoleDetailList": [],
"Policies": [],
}
paginator = iam_client.get_paginator("get_account_authorization_details")
for page in paginator.paginate(Filter=["User"]):
# Always add inline user policies
results["UserDetailList"].extend(page["UserDetailList"])
for page in paginator.paginate(Filter=["Group"]):
results["GroupDetailList"].extend(page["GroupDetailList"])
for page in paginator.paginate(Filter=["Role"]):
results["RoleDetailList"].extend(page["RoleDetailList"])
# Ignore Service Linked Roles
for policy in page["Policies"]:
if policy["Path"] != "/service-role/":
results["RoleDetailList"].append(policy)
for page in paginator.paginate(Filter=["LocalManagedPolicy"]):
# Add customer-managed policies IF they are attached to IAM principals
for policy in page["Policies"]:
if policy["AttachmentCount"] > 0:
results["Policies"].append(policy)
for page in paginator.paginate(Filter=["AWSManagedPolicy"]):
# Add customer-managed policies IF they are attached to IAM principals
for policy in page["Policies"]:
if policy["AttachmentCount"] > 0:
if include_non_default_policy_versions:
results["Policies"].append(policy)
else:
policy_version_list = []
for policy_version in policy.get("PolicyVersionList"):
if policy_version.get("VersionId") == policy.get(
"DefaultVersionId"
):
policy_version_list.append(policy_version)
break
entry = {
"PolicyName": policy.get("PolicyName"),
"PolicyId": policy.get("PolicyId"),
"Arn": policy.get("Arn"),
"Path": policy.get("Path"),
"DefaultVersionId": policy.get("DefaultVersionId"),
"AttachmentCount": policy.get("AttachmentCount"),
"PermissionsBoundaryUsageCount": policy.get(
"PermissionsBoundaryUsageCount"
),
"IsAttachable": policy.get("IsAttachable"),
"CreateDate": policy.get("CreateDate"),
"UpdateDate": policy.get("UpdateDate"),
"PolicyVersionList": policy_version_list,
}
results["Policies"].append(entry)
return results
������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/command/expand_policy.py����������������������������������������0000644�0001751�0000164�00000002243�13702127516�025200� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""
Expands the wildcards (*) on an IAM policy file so it is easier for a human to understand. Example: s3:g* vs s3:GetObject, s3:GetObjectAcl, etc.
"""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
import json
import click
import click_log
from policy_sentry.analysis.expand import get_expanded_policy
logger = logging.getLogger()
click_log.basic_config(logger)
@click.command(
short_help="Expand the * Actions in IAM policy files to improve readability"
)
@click.option(
"--input",
type=click.Path(exists=True),
required=True,
help="Path to the JSON policy file.",
)
@click_log.simple_verbosity_option(logger)
def expand_policy(input): # pylint: disable=redefined-builtin
"""
Expand the * Actions in IAM policy files to improve readability
"""
file = input
with open(file) as json_file:
logger.debug(f"Opening {file}")
data = json.load(json_file)
policy = get_expanded_policy(data)
print(json.dumps(policy, indent=4))
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/command/scan.py�������������������������������������������������0000644�0001751�0000164�00000023200�13702127516�023262� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""
Scan a single account authorization file
"""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
import os
import webbrowser
import json
from pathlib import Path
import yaml
import click
import click_log
from cloudsplaining.shared.constants import EXCLUSIONS_FILE
from cloudsplaining.shared.validation import check_authorization_details_schema
from cloudsplaining.shared.exclusions import Exclusions, DEFAULT_EXCLUSIONS
from cloudsplaining.scan.authorization_details import AuthorizationDetails
from cloudsplaining.output.triage_worksheet import create_triage_worksheet
from cloudsplaining.output.data_file import write_results_data_file
from cloudsplaining.output.report import HTMLReport
logger = logging.getLogger(__name__)
click_log.basic_config(logger)
@click.command(
short_help="Scan a single file containing AWS IAM account authorization details and generate report on "
"IAM security posture. "
)
@click.option(
"--input",
type=click.Path(exists=True),
required=True,
help="Path of IAM account authorization details file",
)
@click.option(
"--exclusions-file",
help="A yaml file containing a list of policy names to exclude from the scan.",
type=click.Path(exists=True),
required=False,
default=EXCLUSIONS_FILE,
)
@click.option(
"--output",
required=False,
type=click.Path(exists=True),
default=os.getcwd(),
help="Output directory.",
)
@click.option(
"--skip-open-report",
required=False,
default=False,
is_flag=True,
help="Don't open the HTML report in the web browser after creating. "
"This helps when running the report in automation.",
)
@click_log.simple_verbosity_option()
# pylint: disable=redefined-builtin
def scan(
input, exclusions_file, output, skip_open_report
): # pragma: no cover
"""
Given the path to account authorization details files and the exclusions config file, scan all inline and
managed policies in the account to identify actions that do not leverage resource constraints.
"""
if exclusions_file:
# Get the exclusions configuration
with open(exclusions_file, "r") as yaml_file:
try:
exclusions_cfg = yaml.safe_load(yaml_file)
except yaml.YAMLError as exc:
logger.critical(exc)
exclusions = Exclusions(exclusions_cfg)
else:
exclusions = DEFAULT_EXCLUSIONS
if os.path.isfile(input):
account_name = Path(input).stem
with open(input) as f:
contents = f.read()
account_authorization_details_cfg = json.loads(contents)
rendered_html_report = scan_account_authorization_details(
account_authorization_details_cfg, exclusions, account_name, output, write_data_files=True
)
html_output_file = os.path.join(output, f"iam-report-{account_name}.html")
logger.info("Saving the report to %s", html_output_file)
if os.path.exists(html_output_file):
os.remove(html_output_file)
with open(html_output_file, "w") as f:
f.write(rendered_html_report)
print(f"Wrote HTML results to: {html_output_file}")
# Open the report by default
if not skip_open_report:
print("Opening the HTML report")
url = "file://%s" % os.path.abspath(html_output_file)
webbrowser.open(url, new=2)
if os.path.isdir(input):
logger.info(
"The path given is a directory. Scanning for account authorization files and generating report."
)
input_files = get_authorization_files_in_directory(input)
for file in input_files:
logger.info(f"Scanning file: {file}")
with open(file) as f:
contents = f.read()
account_authorization_details_cfg = json.loads(contents)
account_name = Path(file).stem
# Scan the Account Authorization Details config
rendered_html_report = scan_account_authorization_details(
account_authorization_details_cfg, exclusions, account_name, output, write_data_files=True
)
html_output_file = os.path.join(output, f"iam-report-{account_name}.html")
logger.info("Saving the report to %s", html_output_file)
if os.path.exists(html_output_file):
os.remove(html_output_file)
with open(html_output_file, "w") as f:
f.write(rendered_html_report)
print(f"Wrote HTML results to: {html_output_file}")
# Open the report by default
if not skip_open_report:
print("Opening the HTML report")
url = "file://%s" % os.path.abspath(html_output_file)
webbrowser.open(url, new=2)
def scan_account_authorization_details(
account_authorization_details_cfg, exclusions, account_name="default", output_directory=None, write_data_files=False
): # pragma: no cover
"""
Given the path to account authorization details files and the exclusions config file, scan all inline and
managed policies in the account to identify actions that do not leverage resource constraints.
"""
logger.debug(
"Identifying modify-only actions that are not leveraging "
"resource constraints..."
)
check_authorization_details_schema(account_authorization_details_cfg)
authorization_details = AuthorizationDetails(account_authorization_details_cfg)
results = authorization_details.missing_resource_constraints(
exclusions, modify_only=True
)
principal_policy_mapping = authorization_details.principal_policy_mapping
# For the IAM Principals tab, add on risk stats per principal
for principal_policy_entry in principal_policy_mapping:
for finding in results:
if principal_policy_entry.get("PolicyName").lower() == finding.get("PolicyName").lower():
principal_policy_entry["Actions"] = len(finding["Actions"])
principal_policy_entry["PrivilegeEscalation"] = len(
finding["PrivilegeEscalation"]
)
principal_policy_entry["DataExfiltrationActions"] = len(
finding["DataExfiltrationActions"]
)
principal_policy_entry["PermissionsManagementActions"] = len(
finding["PermissionsManagementActions"]
)
principal_name = principal_policy_entry["Principal"]
# Customer Managed Policies
if finding.get("Type") == "Policy" and finding.get("ManagedBy") == "Customer" and principal_policy_entry.get("Type") != "Policy":
if "Principals" not in finding:
finding["Principals"] = [principal_name]
else:
if principal_name not in finding["Principals"]:
finding["Principals"].append(principal_name)
# AWS Managed Policies
if finding.get("Type") == "Policy" and finding.get("ManagedBy") == "AWS":
if "Principals" not in finding:
finding["Principals"] = [principal_name]
else:
if principal_name not in finding["Principals"]:
finding["Principals"].append(principal_name)
# Lazy method to get an account ID
account_id = None
for item in results:
if item["ManagedBy"] == "Customer":
account_id = item["AccountID"]
break
html_report = HTMLReport(
account_id=account_id,
account_name=account_name,
results=results,
exclusions_cfg=exclusions,
principal_policy_mapping=principal_policy_mapping
)
rendered_report = html_report.get_html_report()
# Raw data file
if write_data_files:
if output_directory is None:
output_directory = os.getcwd()
raw_data_file = os.path.join(output_directory, f"iam-results-{account_name}.json")
raw_data_filepath = write_results_data_file(results, raw_data_file)
print(f"Raw data file saved: {str(raw_data_filepath)}")
# Principal policy mapping
principal_policy_mapping_file = os.path.join(
output_directory, f"iam-principals-{account_name}.json"
)
principal_policy_mapping_filepath = write_results_data_file(
principal_policy_mapping, principal_policy_mapping_file
)
print(f"Principals data file saved: {str(principal_policy_mapping_filepath)}")
# Create the CSV triage sheet
create_triage_worksheet(account_name, results, output_directory)
return rendered_report
def get_authorization_files_in_directory(directory): # pragma: no cover
"""Get a list of download-account-authorization-files in a directory"""
file_list = [
f for f in os.listdir(directory) if os.path.isfile(os.path.join(directory, f))
]
file_list_with_full_path = []
for file in file_list:
if file.endswith(".json"):
file_list_with_full_path.append(
os.path.abspath(os.path.join(directory, file))
)
new_file_list = []
for file in file_list_with_full_path:
with open(file) as f:
contents = f.read()
account_authorization_details_cfg = json.loads(contents)
valid_schema = check_authorization_details_schema(
account_authorization_details_cfg
)
if valid_schema:
new_file_list.append(file)
return new_file_list
������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/command/scan_policy_file.py�������������������������������������0000644�0001751�0000164�00000011552�13702127516�025647� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""
Scan a single policy file to identify missing resource constraints.
"""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
import json
from pathlib import Path
import yaml
import click
import click_log
from cloudsplaining.output.findings import Findings, PolicyFinding
from cloudsplaining.shared.constants import EXCLUSIONS_FILE
from cloudsplaining.scan.policy_document import PolicyDocument
from cloudsplaining.shared.exclusions import (
Exclusions,
DEFAULT_EXCLUSIONS,
)
logger = logging.getLogger(__name__)
click_log.basic_config(logger)
BOLD = "\033[1m"
RED = "\033[91m"
END = "\033[0m"
@click.command(
short_help="Scan a single policy file to identify identify missing resource constraints."
)
@click.option(
"--input",
type=click.Path(exists=True),
required=True,
help="Path of to the IAM policy file.",
)
@click.option(
"--exclusions-file",
help="A yaml file containing a list of actions to ignore when scanning.",
type=click.Path(exists=True),
required=False,
default=EXCLUSIONS_FILE,
)
@click.option(
"--high-priority-only",
required=False,
default=False,
is_flag=True,
help="If issues are found, only print the high priority risks"
" (Resource Exposure, Privilege Escalation, Data Exfiltration). This can help with prioritization.",
)
@click_log.simple_verbosity_option(logger)
# pylint: disable=redefined-builtin
def scan_policy_file(input, exclusions_file, high_priority_only): # pragma: no cover
"""Scan a single policy file to identify missing resource constraints."""
file = input
# Get the exclusions configuration
with open(exclusions_file, "r") as yaml_file:
try:
exclusions_cfg = yaml.safe_load(yaml_file)
except yaml.YAMLError as exc:
logger.critical(exc)
exclusions = Exclusions(exclusions_cfg)
# Get the Policy
with open(file) as json_file:
logger.debug(f"Opening {file}")
policy = json.load(json_file)
policy_name = Path(file).stem
# Run the scan and get the raw data.
results = scan_policy(policy, policy_name, exclusions)
# There will only be one finding in the results but it is in a list.
results_exist = 0
for finding in results:
if finding["PrivilegeEscalation"]:
print(f"{RED}Issue found: Privilege Escalation{END}")
results_exist += 1
for item in finding["PrivilegeEscalation"]:
print(f"- Method: {item['type']}")
print(f" Actions: {', '.join(item['PrivilegeEscalation'])}\n")
if finding["DataExfiltrationActions"]:
results_exist += 1
print(f"{RED}Issue found: Data Exfiltration{END}")
print(
f"{BOLD}Actions{END}: {', '.join(finding['DataExfiltrationActions'])}\n"
)
if finding["PermissionsManagementActions"]:
results_exist += 1
print(f"{RED}Issue found: Resource Exposure{END}")
print(
f"{BOLD}Actions{END}: {', '.join(finding['PermissionsManagementActions'])}\n"
)
if not high_priority_only:
results_exist += 1
print(f"{RED}Issue found: Unrestricted Infrastructure Modification{END}")
print(f"{BOLD}Actions{END}: {', '.join(finding['Actions'])}")
if results_exist == 0:
print("There were no results found.")
def scan_policy(policy_json, policy_name, exclusions=DEFAULT_EXCLUSIONS):
"""
Scan a policy document for missing resource constraints.
:param exclusions: Exclusions object
:param policy_json: The AWS IAM policy document.
:param policy_name: The name of the IAM policy. Defaults to the filename when used from command line.
:return:
"""
actions_missing_resource_constraints = []
policy_document = PolicyDocument(policy_json)
findings = Findings(exclusions)
for statement in policy_document.statements:
logger.debug("Evaluating statement: %s", statement.json)
if statement.effect == "Allow":
actions_missing_resource_constraints.extend(
statement.missing_resource_constraints_for_modify_actions(exclusions)
)
if actions_missing_resource_constraints:
these_results = list(
dict.fromkeys(actions_missing_resource_constraints)
) # remove duplicates
these_results.sort()
finding = PolicyFinding(
policy_name=policy_name,
arn=policy_name,
actions=these_results,
policy_document=policy_document,
exclusions=exclusions,
)
findings.add_policy_finding(finding)
findings.single_use = True
return finding.json
else:
return []
������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/���������������������������������������������������������0000755�0001751�0000164�00000000000�13702127550�021707� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/__init__.py����������������������������������������������0000644�0001751�0000164�00000000140�13702127516�024015� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# pylint: disable=missing-module-docstring
import logging
logger = logging.getLogger(__name__)
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/data_file.py���������������������������������������������0000644�0001751�0000164�00000001542�13702127516�024175� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Creates a JSON data file containing the results."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import os
import json
# pragma: no cover
def write_results_data_file(results, raw_data_file):
"""
Writes the raw data file containing all the results for an AWS account
:param results: Dictionary containing the scan results for a particular account
:param raw_data_file:
:return:
"""
# Write the output to a results file if that was specified. Otherwise, just print to stdout
if os.path.exists(raw_data_file):
os.remove(raw_data_file)
with open(raw_data_file, "w") as file:
json.dump(results, file, indent=4)
return raw_data_file
��������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/findings.py����������������������������������������������0000644�0001751�0000164�00000052537�13702127516�024100� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Holds all the finding classes"""
import logging
from operator import itemgetter
from policy_sentry.util.arns import get_resource_string, get_account_from_arn, get_resource_path_from_arn
from cloudsplaining.shared.exclusions import (
is_name_excluded,
Exclusions,
DEFAULT_EXCLUSIONS,
)
from cloudsplaining.shared.constants import READ_ONLY_DATA_LEAK_ACTIONS
from cloudsplaining.shared.utils import capitalize_first_character, get_full_policy_path
logger = logging.getLogger(__name__)
class Findings:
"""Holds all the findings"""
def __init__(self, exclusions=DEFAULT_EXCLUSIONS):
self.users = []
self.roles = []
self.groups = []
self.policies = []
self.exclusions = exclusions
self.principal_policy_mapping = []
# Hacky way to determine whether it is running the scan or scan_policy_file command
self.single_use = False
def add_user_finding(self, user_finding):
"""Adds a UserFinding object"""
if not isinstance(user_finding, UserFinding):
raise Exception("Please supply a UserFinding object")
if not user_finding.is_excluded(self.exclusions):
self.users.append(user_finding)
def add_group_finding(self, group_finding):
"""Adds a GroupFinding object"""
if not isinstance(group_finding, GroupFinding):
raise Exception("Please supply a GroupFinding object")
if not group_finding.is_excluded(self.exclusions):
self.groups.append(group_finding)
def add_role_finding(self, role_finding):
"""Adds a RoleFinding object"""
if not isinstance(role_finding, RoleFinding):
raise Exception("Please supply a RoleFinding object")
if not role_finding.is_excluded(self.exclusions):
self.roles.append(role_finding)
def add_policy_finding(self, policy_finding):
"""Adds a PolicyFinding object"""
if not isinstance(policy_finding, PolicyFinding):
raise Exception("Please supply a PolicyFinding object")
if not policy_finding.is_excluded(self.exclusions):
self.policies.append(policy_finding)
@property
def valid_principals(self):
"""Get a list of the principals (Users, Groups, Roles) that are used"""
principals = []
if self.users:
for user_finding in self.users:
principals.append(user_finding.name)
if self.groups:
for group_finding in self.groups:
principals.append(group_finding.name)
if self.roles:
for role_finding in self.roles:
principals.append(role_finding.name)
return principals
def policies_in_use(self):
"""Get a list of policy names that are in use"""
if not self.principal_policy_mapping:
raise Exception(
"Set the principal_policy_mapping attribute before running."
)
these_policies_in_use = []
for principal_policy_entry in self.principal_policy_mapping:
# If they are not excluded:
if principal_policy_entry.get("Type") == "User":
if not self.exclusions.is_principal_excluded(
principal_policy_entry.get("Principal"), "User"
):
if not self.exclusions.is_policy_excluded(
principal_policy_entry.get("PolicyName")
):
these_policies_in_use.append(
principal_policy_entry.get("PolicyName")
)
if principal_policy_entry.get("Type") == "Group":
if not self.exclusions.is_principal_excluded(
principal_policy_entry.get("Principal"), "User"
):
if not self.exclusions.is_policy_excluded(
principal_policy_entry.get("PolicyName")
):
these_policies_in_use.append(
principal_policy_entry.get("PolicyName")
)
if principal_policy_entry.get("Type") == "Role":
if not self.exclusions.is_principal_excluded(
principal_policy_entry.get("Principal"), "Role"
):
if not self.exclusions.is_policy_excluded(
principal_policy_entry.get("PolicyName")
):
these_policies_in_use.append(
principal_policy_entry.get("PolicyName")
)
these_policies_in_use = list(
dict.fromkeys(these_policies_in_use)
) # remove duplicates
these_policies_in_use.sort()
logger.debug(f"Policies in use: {these_policies_in_use}")
return these_policies_in_use
@property
def json(self):
"""Return the JSON representation of the findings"""
these_findings = []
# Users
if self.users:
for finding in self.users:
these_findings.append(finding.json)
# Groups
if self.groups:
for finding in self.groups:
these_findings.append(finding.json)
# Roles
if self.roles:
for finding in self.roles:
these_findings.append(finding.json)
# Policies
policies_in_use = self.policies_in_use()
logger.debug("Policies in use: %s", str(policies_in_use))
policies_in_use_lowercase = [x.lower() for x in policies_in_use]
for finding in self.policies:
if finding.policy_name.lower() in policies_in_use_lowercase:
these_findings.append(finding.json)
else:
print(f"The Policy {finding.policy_name} is not used by any non-excluded principals, "
f"so it is being excluded from the scan.")
# sort it
these_findings = sorted(these_findings, key=itemgetter("PolicyName"))
# print(json.dumps(these_findings, indent=4))
return these_findings
def __len__(self):
length = (
len(self.users) + len(self.groups) + len(self.roles) + len(self.policies)
)
return length
# pylint: disable=too-many-instance-attributes
class Finding:
"""Parent class for the various finding types"""
def __init__(
self,
policy_name,
arn,
actions,
policy_document,
exclusions=DEFAULT_EXCLUSIONS,
assume_role_policy_document=None,
attached_managed_policies=None,
attached_to_principal=None,
):
self.policy_name = policy_name
self.arn = arn
# The `scan` command uses this, whereas the `scan-policy-file` one does not.
if "/" in self.arn:
self.name = get_resource_string(self.arn).split("/")[1]
else:
self.name = policy_name
self.type = capitalize_first_character(
get_resource_string(self.arn).split("/")[0]
)
self.always_exclude_actions = exclusions.exclude_actions
self.exclusions = exclusions
self.actions = self._actions(actions)
self.policy_document = policy_document
# Roles only
self.assume_role_policy_document = assume_role_policy_document
# # Users only
# self.group_membership = self._group_membership(group_membership)
# Principals only (not policies)
self.attached_managed_policies = self._attached_managed_policies(
attached_managed_policies
)
self.attached_to_principal = attached_to_principal
def _actions(self, actions):
"""Set the actions"""
results = []
if self.always_exclude_actions:
for action in actions:
# if is_name_excluded(action.lower(), self.always_exclude_actions):
# If the action is always excluded, don't add it
if self.exclusions.is_action_always_excluded(action):
pass # pragma: no cover
elif self.exclusions.is_action_always_included(action):
results.append(action)
else:
results.append(action)
return results
else:
return actions
def _attached_managed_policies(self, attached_managed_policies):
"""Set the attached managed policies"""
if self.type not in ["User", "Group", "Role"]:
return None
if isinstance(attached_managed_policies, list):
return attached_managed_policies
elif isinstance(attached_managed_policies, str):
return [attached_managed_policies]
elif attached_managed_policies is None:
return None
else:
raise Exception("Please supply the attached policies as a list or string")
@property
def managed_by(self):
"""Determine whether the policy is AWS-Managed or Customer-managed based on a Policy ARN pattern."""
if "arn:aws:iam::aws:" in self.arn:
return "AWS" # pragma: no cover
else:
return "Customer"
@property
def account_id(self):
"""Return the account ID, if applicable."""
if "arn:aws:iam::aws:" in self.arn:
return "N/A" # pragma: no cover
else:
try:
account_id = get_account_from_arn(self.arn)
return account_id
except IndexError as i_e:
logger.debug(i_e)
return "N/A"
@property
def services_affected(self):
"""Return a list of AWS service prefixes affected by the policy in question."""
services_affected = []
for action in self.actions:
service, action_name = action.split(":") # pylint: disable=unused-variable
if service not in services_affected:
services_affected.append(service)
services_affected.sort()
return services_affected
@property
def assume_role_policy_document_json(self):
"""Return the AssumeRole Policy in JSON"""
if self.assume_role_policy_document:
return self.assume_role_policy_document.json
else:
return None
@property
def role_assumable_by_compute_services(self):
"""Determines whether or not the role is assumed from a compute service, and if so which ones."""
if self.assume_role_policy_document:
compute_services = (
self.assume_role_policy_document.role_assumable_by_compute_services
)
return compute_services
else:
return []
@property
def permissions_management_actions_without_constraints(self):
"""Return a list of actions that could cause resource exposure via actions at the 'Permissions management'
access level, if applicable."""
results = []
if self.always_exclude_actions:
for (
action
) in self.policy_document.permissions_management_without_constraints:
if is_name_excluded(action.lower(), self.always_exclude_actions):
pass # pragma: no cover
else:
results.append(action)
return results
else:
return self.policy_document.permissions_management_without_constraints
@property
def privilege_escalation(self):
"""Return a list of actions that could cause Privilege Escalation, if applicable."""
return self.policy_document.allows_privilege_escalation
@property
def data_leak_actions(self):
"""Return a list of actions that could cause data exfiltration, if applicable."""
return self.policy_document.allows_specific_actions_without_constraints(
READ_ONLY_DATA_LEAK_ACTIONS
)
@property
def json(self):
"""Return the JSON representation of the Finding.
This is used in the report output and the results data file."""
result = {
"AccountID": self.account_id,
"ManagedBy": self.managed_by,
"Name": self.name,
"PolicyName": self.policy_name,
"Type": self.type,
"Arn": self.arn,
"AttachedToPrincipal": self.attached_to_principal,
# "ActionsCount": self.actions_count,
# "ServicesCount": self.services_count,
"ActionsCount": len(self.actions),
"ServicesCount": len(self.services_affected),
"Services": self.services_affected,
"Actions": self.actions,
"PolicyDocument": self.policy_document.json,
"AssumeRolePolicyDocument": self.assume_role_policy_document_json,
# These items help with prioritizing triage and remediation.
"AssumableByComputeService": self.role_assumable_by_compute_services,
"PrivilegeEscalation": self.privilege_escalation,
"DataExfiltrationActions": self.data_leak_actions,
"PermissionsManagementActions": self.permissions_management_actions_without_constraints,
# Separate the "Write" and "Tagging" actions in the machine-readable output only
# "WriteActions": self.policy_document.write_actions_without_constraints,
# "TaggingActions": self.policy_document.tagging_actions_without_constraints,
}
return result
class UserFinding(Finding):
"""Findings for users"""
def __init__(
self,
policy_name,
arn,
actions,
policy_document,
group_membership,
exclusions=DEFAULT_EXCLUSIONS,
attached_managed_policies=None,
):
if attached_managed_policies is None:
attached_managed_policies = []
super().__init__(
policy_name,
arn,
actions,
policy_document,
exclusions=exclusions,
attached_managed_policies=attached_managed_policies,
attached_to_principal=get_resource_path_from_arn(arn)
)
self.group_membership = self._group_membership(group_membership)
self.attached_to_principal = get_resource_path_from_arn(self.arn)
# pylint: disable=no-self-use
def _group_membership(self, group_membership):
if isinstance(group_membership, list):
return group_membership
elif isinstance(group_membership, str):
return [group_membership]
elif group_membership is None:
return None
else:
raise Exception("Please supply the group membership as a list or string")
def is_excluded(self, exclusions):
"""Determine whether or not the User in question is excluded"""
if not isinstance(exclusions, Exclusions):
raise Exception("Please supply a Exclusions object")
# (1) If the user is a member of an excluded group, return True
excluded_groups = []
if self.group_membership:
for group in self.group_membership:
if exclusions.is_principal_excluded(group, "Group"):
excluded_groups.append(group)
if excluded_groups:
# return True
return excluded_groups
# (2) If the user is explicitly excluded, return True
if exclusions.is_principal_excluded(self.name, "User"):
logger.debug(f"Excluded: the {self.name} user is explicitly excluded.")
return [self.name]
# Each finding will be limited to one policy - so if this user has multiple risky policies,
# then there will be multiple findings per group
# So, for this finding, we will check if the single PolicyName/path assigned to this group is excluded.
# (3) If the policy attached is excluded
# Policy Name
if exclusions.is_policy_excluded(self.policy_name.lower()):
return [self.policy_name]
# Policy Path
elif exclusions.is_policy_excluded(get_full_policy_path(self.arn)):
return [get_full_policy_path(self.arn)]
# (4) If we made it this far, it's not excluded
else:
return False
class GroupFinding(Finding):
"""Findings for Groups"""
def __init__(
self,
policy_name,
arn,
actions,
policy_document,
members,
exclusions=DEFAULT_EXCLUSIONS,
attached_managed_policies=None,
):
if attached_managed_policies is None:
attached_managed_policies = []
super().__init__(
policy_name,
arn,
actions,
policy_document,
exclusions=exclusions,
attached_managed_policies=attached_managed_policies,
attached_to_principal=get_resource_path_from_arn(arn)
)
# Group members
self.members = members
def is_excluded(self, exclusions):
"""Determine whether or not the Group in question is excluded"""
if not isinstance(exclusions, Exclusions):
raise Exception("Please supply a Exclusions object")
# (1) If there are no more users in the group
members_in_use = []
if self.members:
for member in self.members:
if not exclusions.is_principal_excluded(member, "User"):
members_in_use.append(member)
if len(members_in_use) == 0:
# decision_count += 1
logger.debug(
f"Excluded: the {self.name} group's members are all excluded."
)
return members_in_use
# (2) If the group itself is excluded.
if exclusions.is_principal_excluded(self.name, "Group"):
logger.debug(f"Excluded: the {self.name} group is explicitly excluded.")
return self.name
# Each finding will be limited to one policy - so if this group has multiple risky policies,
# then there will be multiple findings per group
# So, for this finding, we will check if the single PolicyName/path assigned to this group is excluded.
# (3) If the policy attached is excluded
# Policy Name
if exclusions.is_policy_excluded(self.policy_name.lower()):
return self.policy_name
# Policy Path
elif exclusions.is_policy_excluded(get_full_policy_path(self.arn)):
return get_full_policy_path(self.arn)
else:
# (4) If we made it this far, it's not excluded
return False
class RoleFinding(Finding):
"""Findings for roles"""
def __init__(
self,
policy_name,
arn,
actions,
policy_document,
exclusions=DEFAULT_EXCLUSIONS,
assume_role_policy_document=None,
attached_managed_policies=None,
):
if attached_managed_policies is None:
attached_managed_policies = []
super().__init__(
policy_name,
arn,
actions,
policy_document,
exclusions=exclusions,
assume_role_policy_document=assume_role_policy_document,
attached_managed_policies=attached_managed_policies,
attached_to_principal=get_resource_path_from_arn(arn)
)
def is_excluded(self, exclusions):
"""Determine whether or not the Role in question is excluded"""
if not isinstance(exclusions, Exclusions):
raise Exception("Please supply a Exclusions object")
# (1) If the role is explicitly excluded
if exclusions.is_principal_excluded(self.name, "Role"):
logger.debug(f"Excluded: the {self.name} role is explicitly excluded.")
return True
# Each finding will be limited to one policy - so if this user has multiple risky policies,
# then there will be multiple findings per group
# So, for this finding, we will check if the single PolicyName/path assigned to this group is excluded.
# (2) If the policy attached is excluded
# Policy Name
if exclusions.is_policy_excluded(self.policy_name.lower()):
return self.policy_name
# Policy Path
elif exclusions.is_policy_excluded(get_full_policy_path(self.arn)):
return get_full_policy_path(self.arn)
# (4) If we made it this far, it's not excluded
else:
return False
class PolicyFinding(Finding):
"""Findings for Policies"""
def __init__(
self,
policy_name,
arn,
actions,
policy_document,
exclusions=DEFAULT_EXCLUSIONS,
assume_role_policy=None,
attached_managed_policies=None,
):
super().__init__(
policy_name,
arn,
actions,
policy_document,
exclusions=exclusions,
assume_role_policy_document=assume_role_policy,
attached_managed_policies=attached_managed_policies,
)
def is_excluded(self, exclusions):
"""Determine whether or not the Policy in question is excluded"""
if not isinstance(exclusions, Exclusions):
raise Exception("Please supply a Exclusions object")
# (1) If the policy attached is excluded
# Policy Name
if exclusions.is_policy_excluded(self.policy_name.lower()):
return [self.policy_name]
# Policy Path
elif exclusions.is_policy_excluded(get_full_policy_path(self.arn)):
return [get_full_policy_path(self.arn)]
# (2) If we made it this far, it's not excluded
else:
return False
�����������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/report.py������������������������������������������������0000644�0001751�0000164�00000012411�13702127516�023575� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Creates the HTML Reports"""
import os
import codecs
import datetime
import markdown
import yaml
from jinja2 import Environment, FileSystemLoader
from cloudsplaining.bin.version import __version__
class HTMLReport:
"""
HTML Report
"""
# pylint: disable=too-many-instance-attributes
def __init__(self, account_name, account_id, exclusions_cfg, results, principal_policy_mapping):
self.account_name = account_name
self.account_id = account_id
self.scan_results = results
self.principal_policy_mapping = principal_policy_mapping
self.exclusions_cfg = exclusions_cfg
self.report_generated_time = datetime.datetime.now().strftime("%Y-%m-%d")
# Calculate ratio of policies with PrivEsc, Permissions management, or Data leak potential
self.policies_with_data_leak_potential = 0
self.policies_with_permissions_management = 0
self.policies_with_privilege_escalation = 0
for finding in results:
# These are stats we care about regardless of who manages it, as they help with prioritization
if finding["DataExfiltrationActions"]:
self.policies_with_data_leak_potential += 1
if finding["PrivilegeEscalation"]:
self.policies_with_privilege_escalation += 1
if finding["PermissionsManagementActions"]:
self.policies_with_permissions_management += 1
def get_html_report(self):
"""Get the HTML Report as a string"""
report_documentation = ReportDocumentation()
# Formatted results to feed into the HTML
iam_report_results_formatted = dict(
account_name=self.account_name,
account_id=self.account_id,
report_generated_time=self.report_generated_time,
cloudsplaining_version=__version__,
results=self.scan_results,
principal_policy_mapping=self.principal_policy_mapping,
overview_write_up=report_documentation.overview_html,
triage_guidance_write_up=report_documentation.triage_guidance_html,
remediation_guidance_write_up=report_documentation.validation_guidance_html,
glossary_write_up=report_documentation.glossary_html,
policies_with_data_leak_potential=self.policies_with_data_leak_potential,
policies_with_privilege_escalation=self.policies_with_privilege_escalation,
policies_with_permissions_management=self.policies_with_permissions_management,
exclusions_configiuration=yaml.dump(self.exclusions_cfg),
)
# HTML Report template
template_path = os.path.join(os.path.dirname(__file__), "templates")
env = Environment(loader=FileSystemLoader(template_path)) # nosec
template = env.get_template("template.html")
return template.render(t=iam_report_results_formatted)
class ReportDocumentation:
"""Holds the rendered Markdown documentation that goes along with the report"""
def __init__(self):
# MARKDOWN WRITE-UPS
# Leverage this documentation for setting HTML in the markdown file.
# We are using markdown because it's just an easier way to modify the general reusable text content.
# https://python-markdown.github.io/extensions/md_in_html/
# 1. Overview
overview_file = codecs.open(
os.path.join(
os.path.dirname(__file__), "templates", "guidance", "1-overview.md"
),
mode="r",
encoding="utf-8",
)
self.overview_html = markdown.markdown(
overview_file.read(), extensions=["markdown.extensions.extra"]
)
# 2. Triage guidance
triage_guidance_file = codecs.open(
os.path.join(
os.path.dirname(__file__), "templates", "guidance", "2-triage-guidance.md"
),
mode="r",
encoding="utf-8",
)
self.triage_guidance_html = markdown.markdown(
triage_guidance_file.read(), extensions=["markdown.extensions.extra"]
)
# 3. Remediation Guidance
remediation_guidance_file = codecs.open(
os.path.join(
os.path.dirname(__file__),
"templates",
"guidance",
"3-remediation-guidance.md",
),
mode="r",
encoding="utf-8",
)
self.remediation_guidance_html = markdown.markdown(
remediation_guidance_file.read(), extensions=["markdown.extensions.extra"]
)
# 4. Validation
validation_guidance_file = codecs.open(
os.path.join(
os.path.dirname(__file__), "templates", "guidance", "4-validation.md"
),
mode="r",
encoding="utf-8",
)
self.validation_guidance_html = markdown.markdown(
validation_guidance_file.read(), extensions=["markdown.extensions.extra"]
)
# 5. Glossary
glossary_file = codecs.open(
os.path.join(os.path.dirname(__file__), "templates", "guidance", "glossary.md"),
mode="r",
encoding="utf-8",
)
self.glossary_html = markdown.markdown(
glossary_file.read(), extensions=["markdown.extensions.extra"]
)
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/�����������������������������������������������0000755�0001751�0000164�00000000000�13702127550�023705� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/analysis/��������������������������������������0000755�0001751�0000164�00000000000�13702127550�025530� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/analysis/aws-managed.html����������������������0000644�0001751�0000164�00000006667�13702127516�030623� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������{% for finding in t["results"] %}
{% if finding["ManagedBy"] == "AWS" %}
{% if finding["PrivilegeEscalation"]|length > 0 or
finding["DataExfiltrationActions"]|length > 0 or
finding["PermissionsManagementActions"]|length > 0
%}
{% if finding["PrivilegeEscalation"]|length > 0 or
finding["DataExfiltrationActions"]|length > 0 or
finding["PermissionsManagementActions"]|length > 0 or
finding["AssumableByComputeService"]|length > 0
%}
Type: {% if finding["Type"] == "Policy" %}{{ finding["ManagedBy"] }}-Managed {{ finding["Type"] }}{% else %}Inline {{ finding["Type"] }} Policy{% endif %}
{% if finding["Type"] == "Policy" %}
{% if "Principals" in finding %}
Attached to Principal(s):
{% for principal in finding["Principals"] %}
- {{ principal }}{% endfor %}
{% endif %}
{% else %}
{% if finding["AttachedToPrincipal"] %}
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/guidance/��������������������������������������0000755�0001751�0000164�00000000000�13702127550�025464� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/guidance/1-overview.md�������������������������0000644�0001751�0000164�00000001176�13702127516�030021� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������This report contains the security assessment results from [Cloudsplaining](https://github.com/salesforce/cloudsplaining), which maps out the IAM risk landscape in a report, identifies where resource ARN constraints are not used, and identifies other risks in IAM policies like [Privilege Escalation](#definition-privilege-escalation), [Resource Exposure](#definition-resource-exposure), [Infrastructure Modification](#definition-infrastructure-modification), and [Data Exfiltration](#definition-data-exfiltration). Remediating these issues, where necessary, will help to limit the blast radius in the case of compromised AWS credentials.
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/guidance/2-triage-guidance.md������������������0000644�0001751�0000164�00000026365�13702127516�031213� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
Understanding Context
It's essential to understand the context behind the findings that the report generates. Understanding the context behind the findings aids the assessor in triaging the results accurately.
This report generates findings on Policies that do not leverage resource constraints and identifies some attributes to help prioritize which ones to address - such as Privilege Escalation, Resource Exposure, and Data Exfiltration. These results help you to identify your IAM threat landscape and reduce blast radius. In the event of credential compromise, you can prevent an attacker from exploiting the risks mentioned above, in addition to preventing mass deletion, destruction, or modification of existing infrastructure.
However, this tool does not attempt to understand the context behind everything in your AWS account. It's possible to understand the context behind some of these things programmatically - whether the policy is applied to an instance profile, whether the policy is attached, whether inline IAM policies are in use, and whether or not AWS Managed Policies are in use. **Only you know the context behind the design of your AWS infrastructure and the IAM strategy**.
For example, an AWS Lambda policy used as a simple service checking the configuration of AWS infrastructure might be a good use case for resource constraints. Conversely, perhaps you applied the AdministratorAccess AWS-managed policy to an Instance Profile so that an EC2 instance can run Terraform to provision AWS resources via Infrastructure as Code. In the second example, the role is extremely permissive **by design** - and a tool can't automatically understand that context.
As such, the tool aims to:
Map out your risk landscape of IAM identity-based policies, enumerating the potential risks for a full IAM threat model
Identify where you can reduce the blast radius in the case of credentials compromise
Help you prioritize which ones to remediate
Provide a straightforward workflow to remediate
Provide a sufficient exclusions mechanism to programmatically define where deviations from resource constraints are by design
Assessment Recap
To recap: you've followed these steps to generate this report:
Downloaded the Account Authorization details JSON file
This generates three files: (1) The single-file HTML report, (2) The triage CSV worksheet, and (3) The raw JSON data file
Triaging workflow
An assessor can follow this general workflow:
Open a ticket in your organization's project management tool of choice (for example, JIRA or Salesforce) in the AWS account owner's project
Attach the HTML report, JSON Data file, and CSV worksheet
Ask the service/account owner team to fill out the Triage worksheet
When you ask the service/account owner team to fill out the Triage CSV worksheet, you can use some text like the following:
> As part of our security assessment, our team ran Cloudsplaining on your AWS account. Cloudsplaining maps out the IAM risk landscape in a report, identifies where resource ARN constraints are not in use, and identifies other risks in IAM policies like Privilege Escalation, Data Exfiltration, and Resource Exposure/Permissions management. Remediating these issues, where applicable, will help to limit the blast radius in the case of compromised AWS credentials.
> We request that you review the HTML report and fill out the "Justification" field in the Triage worksheet. Based on the corresponding details in the HTML report, provide either (1) A justification on why the result is a False Positive, or (2) Identify that it is a legitimate finding.
Triaging considerations
When triaging your results, consider some of the factors listed below as you identify False Positives vs. legitimate findings. **There are some scenarios where `"Resource": "*"` access is by design and is therefore a false positive. This section covers some of the common scenarios.**
**Infrastructure Creation roles**:
IAM roles that create infrastructure via Infrastructure as Code Technologies (for example, Terraform or CloudFormation) require high permission levels to provision AWS infrastructure. These will usually be false positives. When you see these instances, make sure that these roles are adequately protected. For instance, make sure that roles within the AWS account are not able to assume this role or affect its configuration in any way. Additionally, consider restricting the trust policy so that a set of explicitly stated IAM principals are the only ones who can assume that role. Take special care to audit instances of `sts:AssumeRole` within this AWS account.
**System roles vs. User Roles**: System roles - IAM Roles applied to compute services, such as EC2 Instance Profiles, ECS Task Execution roles, or Lambda Task Execution roles - should almost always leverage resource ARN constraints for actions that perform "Write" actions. Exceptions to this could include Infrastructure provisioning or other edge cases.
Conversely, user roles will almost always be used against `*` resources for the sake of convenience, innovation, and avoiding overly restrictive limitations. In the user role scenario, consider:
Design context: is it appropriate? (For instance, maybe all your user roles don't need iam:*)
Environment: If this is a Dev environment, frequently-used user roles probably allow more permissions for innovation purposes. However, in later environments - especially production - commonly used user roles should be read-only - or the more permissive ones should be for break-glass scenarios only.
**Organization-specific results**
For example, perhaps you allow kms:Decrypt for * resources (by design) in your organization for one reason or another. Cloudsplaining flags this as a result. However, there are mitigating controls in place. Firstly, you leverage strict resource-based KMS key policies to lock down all KMS keys, explicitly stating individual IAM principals that are allowed to use them. Secondly, you provision all KMS keys with CloudFormation or Terraform, so you are confident that this pattern is consistent across all KMS keys in your AWS accounts. Therefore, `kms:Decrypt` to `*` resources is not a finding you are concerned about. In this case, you decide it is acceptable to exclude `kms:Decrypt` from your results.
Common False Positive Scenarios
**Conditions Logic**:
This tool does not evaluate [IAM Conditions](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_condition.html) logic. If your policies use wildcard resources but restrict according to condition keys, then it's possible this is a false positive. However, you might want to double-check the accuracy of the conditions logic in those IAM policies. While IAM conditions can be extremely powerful, implementation is also prone to human error. We suggest leveraging [Parliament by Duo Labs](https://github.com/duo-labs/parliament/) (courtesy of [Scott Piper](https://twitter.com/0xdabbad00)), to lint your policies for accuracy - especially when IAM conditions are in use.
**`logs:CreateLogGroup` and `logs:PutLogEvent`**:
Depending on how your organization approaches CloudWatch Logs Agent configuration, IAM, and CloudWatch Logs Group naming conventions, it is sometimes near-impossible to prevent cross-contamination of logs or Log Injection to the Log Streams from other instance IDs. Cross-Contamination of CloudWatch Logs is an issue of its own that is definitely beyond the scope of this document - but consider this as a potential limitation by AWS when trying to identify a remediation plan.
Building the Exclusions File
After you have identified the False Positives, add the False Positive criteria to your custom Cloudsplaining exclusions file. The False Positives generally fall into one of two categories:
False positives that will occur across all of your AWS accounts, due to your organization-wide implementation strategy
False positives specific to this AWS account
To make the exclusions file, create a YAML file that we will use to list out exclusions with the `create-exclusions-file` command.
```bash
cloudsplaining create-exclusions-file
```
This will generate a file titled `exclusions.yml` in your current directory.
The default exclusions file contains these contents:
```yaml
# Policy names to exclude from evaluation
# Suggestion: Add policies here that are known to be overly permissive by design, after you run the initial report.
policies:
- "AWSServiceRoleFor*"
- "*ServiceRolePolicy"
- "*ServiceLinkedRolePolicy"
- "AdministratorAccess" # Otherwise, this will take a long time
- "service-role*"
- "aws-service-role*"
# Don't evaluate these roles, users, or groups as part of the evaluation
roles:
- "service-role*"
- "aws-service-role*"
users:
- ""
groups:
- ""
# Read-only actions to include in the results, such as s3:GetObject
# By default, it includes Actions that could lead to Data Leaks
include-actions:
- "s3:GetObject"
- "ssm:GetParameter"
- "ssm:GetParameters"
- "ssm:GetParametersByPath"
- "secretsmanager:GetSecretValue"
# Write actions to include from the results, such as kms:Decrypt
exclude-actions:
- ""
```
Add whatever values you want to the above depending on your organization's context.
* Under `policies`, list the path of policy names that you want to exclude.
* If you want to exclude a role titled `MyRole`, list `MyRole` or `MyR*` in the `roles` list.
* You can follow the same approach for `users` and `groups` list.
* Now, run the scan to generate a *new* Cloudsplaining report that considers your exclusions criteria. This way, you are working with a report version that consists of True Positives only.
```bash
cloudsplaining scan --input default.json --exclusions-file exclusions.yml
```
You can now proceed to the Remediation stage.
���������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/guidance/3-remediation-guidance.md�������������0000644�0001751�0000164�00000006262�13702127516�032233� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
Prioritizing Remediation
Depending on the existing workload of the engineering team addressing your concerns, the team might ask to address high priority items first rather than addressing all items, especially if the report is quite large. In this scenario, consider instructing the team to address High Priority Risks and the usage of AWS-Managed Policies first.
**High priority risks**:
These include Privilege Escalation, Data Exfiltration, and Potential Resource Exposure/Permissions management. This report highlights each finding that has these high priority risks.
**Moving from AWS Managed Policies over to custom policies**:
AWS managed policies always include access to `*` resources because AWS provides these same policies universally to all customer accounts. If this report flags any AWS-managed policies, it means that the account/service owner team will not only have to implement resource constraints - they will have to create a custom IAM policy to do so. To limit this work, it is best to migrate away from the root cause of the problem - using AWS managed policies.
You can then queue the work for remediating the other Customer-managed policies that do not have the High-Priority Risks attributes. Implementing resource ARN constraints for True Positives is still important, since overly permissive "Write" actions can cause modification or deletion of AWS resources by a bad actor with compromised credentials, resulting in downtime.
Remediating the Findings
We suggest two options for remediating each finding:
Leveraging [Policy Sentry](https://github.com/salesforce/policy_sentry/), courtesy of Kinnaird McQuade, which generates policies with resource ARN constraints at user-specified access levels automagically.
Manually rewriting the policies
**Leveraging Policy Sentry**
For guidance on how to use Policy Sentry, please see the documentation [here](https://github.com/salesforce/policy_sentry/#writing-secure-policies-based-on-resource-constraints-and-access-levels). This is highly suggested - within 10 minutes of learning the tool, creating a secure IAM policy becomes a matter of:
Generating the YAML template with `policy_sentry create-template --output-file crud.yml --template-type crud`
Literally copying/pasting resource ARNs into the template
**Manually rewriting the IAM Policies**
For guidance on how to write secure IAM Policies by hand, see the tutorial [here](https://engineering.salesforce.com/salesforce-cloud-security-automating-least-privilege-in-aws-iam-with-policy-sentry-b04fe457b8dc#6997). Just be aware - you'll spend a lot of time looking at the [AWS Documentation on IAM Actions, Resources, and Condition Keys](https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_actions-resources-contextkeys.html), which can become quite tedious and time-consuming.
����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/guidance/4-validation.md�����������������������0000644�0001751�0000164�00000003325�13702127516�030306� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
Validating remediated policies
After you've rewritten your IAM policy, we suggest two options for validating that it will pass Cloudsplaining and alleviate any remaining concerns:
Run Cloudsplaining's scan-policy-file command, which scans a single JSON policy file instead of the entire AWS Account's Authorization details.
Using Cloudsplaining to Validate your Remediated Policies
You can validate that your remediated policy passes Cloudsplaining by running the following command:
```cloudsplaining scan-policy-file --input policy.json --exclusions-file exclusions.yml```
When there are no more results, it passes!
Using Parliament to Lint your Policies
parliament is an AWS IAM linting library. It reviews policies looking for problems such as:
malformed JSON
missing required elements
incorrect service prefix and action names
incorrect resources or conditions for the actions provided
type mismatches
bad policy patterns
This library duplicates (and adds to!) much of the functionality in the web console page when reviewing IAM policies in the browser.
You can use Parliament to scan your IAM policy with the following command:
```parliament --file policy.json```
�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/guidance/glossary.md���������������������������0000644�0001751�0000164�00000021735�13702127516�027663� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
Impact
The impact the risk would have on an organization if such a vulnerability were successfully exploited is rated according to criteria listed below. Note that these ratings are based on NIST 800-30 impact definitions.
* **Critical**: The issue causes multiple severe or catastrophic effects on operations, assets or other organizations.
* **High**: Causes produces severe degradation in mission capability to the point that the organization is not able to perform primary functions or results in damage to organizational assets.
* **Medium**: Trigger degradation in mission capability to an extent the application is able to perform its primary functions, but their effectiveness is reduced and there may be damage to the organization's assets.
* **Low**: Results in limited degradation in mission capability; the organization is able to perform its primary functions, but their effectiveness is noticeably reduced and may result in minor damage to the organization's assets.
Privilege Escalation
These policies allow a combination of IAM actions that allow a principal with these permissions to escalate their privileges - for example, by creating an access key for another IAM user, or modifying their own permissions. This research was pioneered by [Spencer Gietzen](https://twitter.com/SpenGietz) at Rhino Security Labs. Remediation Guidance can be found [here](https://rhinosecuritylabs.com/aws/aws-privilege-escalation-methods-mitigation/).
Resource Exposure
Resource Exposure actions allow modification of Permissions to [resource-based policies](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_identity-vs-resource.html) or otherwise can expose AWS resources to the public via similar actions that can lead to resource exposure - for example, the ability to modify [AWS Resource Access Manager](https://docs.aws.amazon.com/ram/latest/userguide/what-is.html).
Infrastructure Modification
Infrastructure Modification describes IAM actions with "modify" capabilities, and can therefore lead to [Resource Hijacking](https://attack.mitre.org/techniques/T1496/), unauthorized creation of Infrastructure, Backdoor creation, and/or modification of existing resources which can result in downtime.
Data Exfiltration
Policies with Data leak potential allow certain read-only IAM actions without resource constraints, such as `s3:GetObject`, `ssm:GetParameter*`, or `secretsmanager:GetSecretValue`. Unrestricted `s3:GetObject` permissions has a long history of customer data leaks. `ssm:GetParameter*` and `secretsmanager:GetSecretValue` are both used to access secrets. `rds:CopyDBSnapshot` and `rds:CreateDBSnapshot` can be used to exfiltrate RDS database contents.
Roles Assumable by Compute Services
IAM Roles can be assumed by AWS Compute Services (such as EC2, ECS, EKS, or Lambda) can present greater risk than user-defined roles, especially if the AWS Compute service is on an instance that is directly or indirectly exposed to the internet. Flagging these roles is particularly useful to penetration testers (or attackers) under certain scenarios. For example, if an attacker obtains privileges to execute [ssm:SendCommand](https://docs.aws.amazon.com/systems-manager/latest/APIReference/API_SendCommand.html) and there are privileged EC2 instances with the SSM agent installed, they can effectively have the privileges of those EC2 instances. Remote Code Execution via AWS Systems Manager Agent was already a known escalation/exploitation path, but Cloudsplaining can make the process of identifying theses cases easier.
Trust Policy
A JSON policy document in which you define the principals that you trust to assume the role. A role trust policy is a required resource-based policy that is attached to a role in IAM. The principals that you can specify in the trust policy include users, roles, accounts, and services.
This definition was taken from the AWS Documentation [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_terms-and-concepts.html#term_trust-policy).
Principal
An entity in AWS that can perform actions and access resources. A principal can be an AWS account root user, an IAM user, or a role.
Role
An IAM identity that you can create in your account that has specific permissions. An IAM role has some similarities to an IAM user. Roles and users are both AWS identities with permissions policies that determine what the identity can and cannot do in AWS. However, instead of being uniquely associated with one person, a role is intended to be assumable by anyone who needs it. Also, a role does not have standard long-term credentials such as a password or access keys associated with it. Instead, when you assume a role, it provides you with temporary security credentials for your role session.
We are particularly interested in roles used for **compute services** - i.e., Compute Service Roles.
This definition was taken from the AWS Documentation [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/id_roles_terms-and-concepts.html#iam-term-role).
Managed Policy
There are two types of Managed Policies: AWS-managed policies and Customer-managed policies. They are described below.
Criteria for selecting Managed Policies versus Inline policies can be found in the AWS documentation [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_managed-vs-inline.html#choosing-managed-or-inline).
Customer-managed policy
AWS documentation on Customer-managed policies can be found [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_managed-vs-inline.html#customer-managed-policies).
The following diagram illustrates customer managed policies. Each policy is an entity in IAM with its own Amazon Resource Name (ARN) that includes the policy name. Notice that the same policy can be attached to multiple principal entities—for example, the same DynamoDB-books-app policy is attached to two different IAM roles.
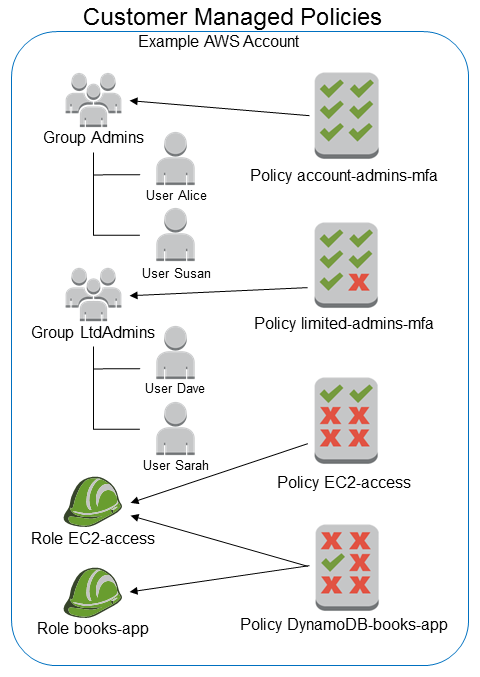
AWS-managed policy
An AWS managed policy is a standalone policy that is created and administered by AWS. Standalone policy means that the policy has its own Amazon Resource Name (ARN) that includes the policy name. For example, arn:aws:iam::aws:policy/IAMReadOnlyAccess is an AWS managed policy.
AWS documentation on AWS-managed policies can be found [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_managed-vs-inline.html#aws-managed-policies).
The following diagram (taken from the AWS documentation) illustrates AWS managed policies. The diagram shows three AWS managed policies: AdministratorAccess, PowerUserAccess, and AWSCloudTrailReadOnlyAccess. Notice that a single AWS managed policy can be attached to principal entities in different AWS accounts, and to different principal entities in a single AWS account.
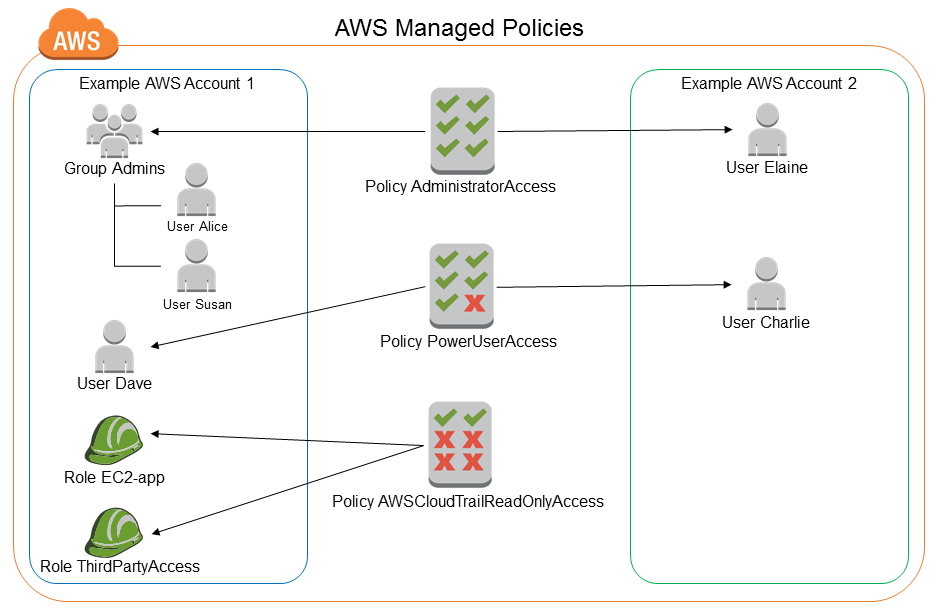
Inline Policy
An inline policy is a policy that's embedded in an IAM identity (a user, group, or role). That is, the policy is an inherent part of the identity. You can create a policy and embed it in a identity, either when you create the identity or later.
AWS documentation on inline policies can be found [here](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_managed-vs-inline.html#inline-policies).
The following diagram illustrates inline policies. Each policy is an inherent part of the user, group, or role. Notice that two roles include the same policy (the DynamoDB-books-app policy), but they are not sharing a single policy; each role has its own copy of the policy.
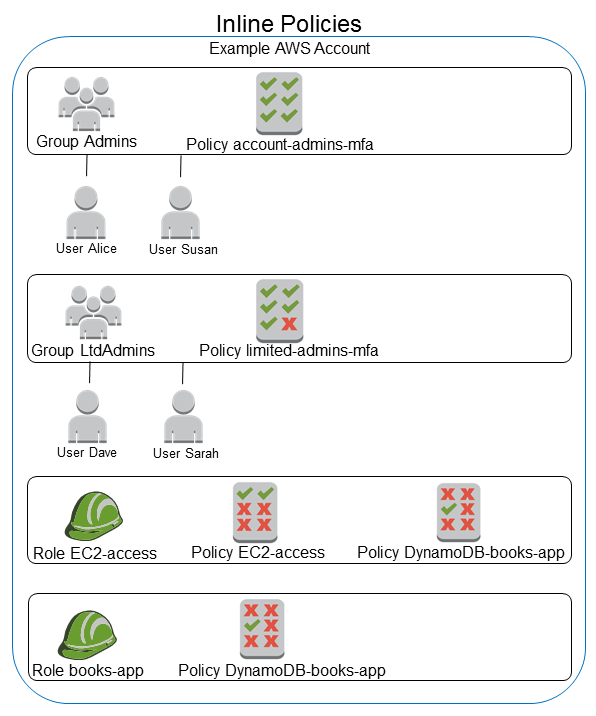
Inline policies are useful if you want to maintain a strict one-to-one relationship between a policy and the identity that it's applied to. For example, you want to be sure that the permissions in a policy are not inadvertently assigned to an identity other than the one they're intended for. When you use an inline policy, the permissions in the policy cannot be inadvertently attached to the wrong identity. In addition, when you use the AWS Management Console to delete that identity, the policies embedded in the identity are deleted as well. That's because they are part of the principal entity.
�����������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/guidance/guidance.html�������������������������0000644�0001751�0000164�00000000641�13702127516�030134� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
The following table shows a list of AWS-managed IAM Policies that (1) have findings and (2) are currently used in the account.
If the policy contains IAM Actions - or combinations of actions - that fall under certain risk categories - Privilege Escalation, Resource Exposure, Infrastructure Modification, and Data Exfiltration - then the number of occurrences per-policy and per-risk is included in the table. If there are no findings for a particular policy, or if the policy is not attached to any IAM Principals, then the policy is not included in the findings.
Each of the aforementioned attributes can be used to prioritize which risks to address first. For more information, see the Prioritization Guidance and Triaging Considerations. Consider using all of the Guidance criteria when reviewing this report as well.
Note that policies or IAM Principals excluded from the scan will not show up in the table at all. Please refer to the Exclusions configuration to see which ones were excluded. To view the list of IAM Principals and their associated policies, see the IAM Principals Tab.
The following table shows a list of Customer created IAM Policies that are currently used in the account - both Managed Policies and Inline Policies. If the policy is an inline policy, the table indicates the IAM Principal that the inline policy is associated with. It only includes policies that (1) have findings and (2) are currently used in the account.
If the policy contains IAM Actions - or combinations of actions - that fall under certain risk categories - Privilege Escalation, Resource Exposure, Infrastructure Modification, and Data Exfiltration - then the number of occurrences per-policy and per-risk is included in the table. If there are no findings for a particular policy, or if the policy is not attached to any IAM Principals, then the policy is not included in the findings.
If the IAM principal is a Role and is assumable by a Compute Service - ec2, ecs-tasks, lambda, or eks - then that is indicated in the table as well.
Each of the aforementioned attributes can be used to prioritize which risks to address first. For more information, see the Prioritization Guidance and Triaging Considerations. Consider using all of the Guidance criteria when reviewing this report as well.
Note that policies or IAM Principals excluded from the scan will not show up in the table at all. Please refer to the Exclusions configuration to see which ones were excluded. To view the list of IAM Principals and their associated policies, see the IAM Principals Tab.
This report contains the security assessment results from Cloudsplaining, which maps out the IAM risk landscape in a report, identifies where resource ARN constraints are not used, and identifies other risks in IAM policies like Privilege Escalation, Resource Exposure, Infrastructure Modification, and Data Exfiltration. Remediating these issues, where necessary, will help to limit the blast radius in the case of compromised AWS credentials.
If the IAM principal is a Role and is assumable by a Compute Service - ec2, ecs-tasks, lambda, or eks - then that is indicated in the table as well.
Note that policies that were excluded from the scan will not have their statistics shown in the table. Please refer to the Exclusions configuration to see which ones were excluded.
{% if principal["GroupMembership"] %}{% if principal["GroupMembership"]|length > 0 %}{% for group in principal["GroupMembership"] %}{{ group }}{% if not loop.last %}, {% endif %}{% endfor %}{% endif %}{% endif %}
{% endfor %}
������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/templates/template.html����������������������������������0000644�0001751�0000164�00000045604�13702127516�026421� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
Cloudsplaining: AWS IAM Policy Audit Report
In-depth analysis: Customer-Managed and Inline Policies
{% include 'analysis/customer-managed.html' %}
Findings: AWS-Managed Policies
{% include 'summary/aws-managed.html' %}
In-depth analysis: AWS-Managed Policies
{% include 'analysis/aws-managed.html' %}
Guidance
{% include 'guidance/guidance.html' %}
Appendix
Glossary
{% include 'appendix/glossary.html' %}
Exclusions configuration
{% include 'appendix/exclusions.html' %}
References
{% include 'appendix/references.html' %}
����������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/output/triage_worksheet.py��������������������������������������0000644�0001751�0000164�00000004501�13702127516�025631� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Creates a triage CSV worksheet for account owners to fill out. This helps with identifying false positives."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import os
import csv
from policy_sentry.util.arns import get_resource_string
def create_triage_worksheet(account_name, results, output_directory):
"""
Create a triage spreadsheet for account owners to fill out. They can specify whether it is a false positive
depending on context or whether or not it needs to be fixed.
"""
triage_spreadsheet_file = os.path.join(
output_directory, f"iam-triage-{account_name}.csv"
)
csv_fieldnames = [
"PolicyName",
"Type",
"ManagedBy",
"Services", # ServicesCount
"Actions", # ActionsCount
"Justification",
]
if os.path.exists(triage_spreadsheet_file):
os.remove(triage_spreadsheet_file)
with open(triage_spreadsheet_file, "w", newline="") as csv_file:
writer = csv.DictWriter(csv_file, fieldnames=csv_fieldnames)
writer.writeheader()
# Write customer findings first
for finding in results:
if finding["ManagedBy"] == "Customer":
entry = {
"PolicyName": finding["PolicyName"],
"Type": get_resource_string(finding["Arn"]).split("/")[0],
"ManagedBy": finding["ManagedBy"],
"Services": finding["ServicesCount"],
"Actions": finding["ActionsCount"],
"Justification": "",
}
writer.writerow(entry)
# Write AWS findings second
for finding in results:
if finding["ManagedBy"] == "AWS":
entry = {
"PolicyName": finding["PolicyName"],
"Type": "Policy",
"ManagedBy": finding["ManagedBy"],
"Services": finding["ServicesCount"],
"Actions": finding["ActionsCount"],
"Justification": "",
}
writer.writerow(entry)
print(f"Use this spreadsheet to triage results: {triage_spreadsheet_file}")
�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/�����������������������������������������������������������0000755�0001751�0000164�00000000000�13702127551�021274� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/__init__.py������������������������������������������������0000644�0001751�0000164�00000000140�13702127516�023401� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# pylint: disable=missing-module-docstring
import logging
logger = logging.getLogger(__name__)
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/assume_role_policy_document.py�����������������������������0000644�0001751�0000164�00000011463�13702127516�027447� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Represents the AssumeRole Trust Policy. This is mainly used for identifying whether roles are assumable via AWS compute services."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
from cloudsplaining.shared.constants import SERVICE_PREFIXES_WITH_COMPUTE_ROLES
logger = logging.getLogger(__name__)
class AssumeRolePolicyDocument:
"""
Holds the AssumeRole/Trust Policy document
"""
def __init__(self, policy):
statement_structure = policy.get("Statement", [])
self.policy = policy
self.statements = []
# leaving here but excluding from tests because IAM Policy grammar dictates that it must be a list
if not isinstance(statement_structure, list): # pragma: no cover
statement_structure = [statement_structure]
for statement in statement_structure:
self.statements.append(AssumeRoleStatement(statement))
@property
def json(self):
"""Return the AssumeRole Policy in JSON"""
return self.policy
@property
def role_assumable_by_compute_services(self):
"""Determines whether or not the role is assumed from a compute service, and if so which ones."""
assumable_by_compute_services = []
for statement in self.statements:
if statement.role_assumable_by_compute_services:
assumable_by_compute_services.extend(
statement.role_assumable_by_compute_services
)
return assumable_by_compute_services
class AssumeRoleStatement:
"""
Statements in an AssumeRole/Trust Policy document
"""
def __init__(self, statement):
self.json = statement
self.statement = statement
self.effect = statement["Effect"]
self.actions = self._assume_role_actions()
self.principals = self._principals()
# self.not_principal = statement.get("NotPrincipal")
if statement.get("NotPrincipal"):
logger.critical( # pragma: no cover
"NotPrincipal is used in the IAM AssumeRole Trust Policy. "
"This should NOT be used. We suggest reviewing it ASAP."
)
def _assume_role_actions(self):
"""Verifies that this is limited to just sts:AssumeRole"""
actions = self.statement.get("Action")
if not actions:
logger.debug("The AssumeRole Policy has no actions in it.")
return []
if not isinstance(actions, list):
actions = [actions]
return actions
def _principals(self):
"""Extracts all principals from IAM statement.
Should handle these cases:
"Principal": "value"
"Principal": ["value"]
"Principal": { "AWS": "value" }
"Principal": { "AWS": ["value", "value"] }
"Principal": { "Service": "value" }
"Principal": { "Service": ["value", "value"] }
Return: Set of principals
"""
principals = []
principal = self.statement.get("Principal", None)
if not principal:
# It is possible not to define a principal, AWS ignores these statements.
return principals # pragma: no cover
if isinstance(principal, dict):
if "AWS" in principal:
if isinstance(principal["AWS"], list):
principals.extend(principal["AWS"])
else:
principals.append(principal["AWS"])
if "Service" in principal:
if isinstance(principal["Service"], list):
principals.extend(principal["Service"])
else:
principals.append(principal["Service"])
else:
principals.append(principal)
# principals = list(principals).sort()
return principals
@property
def role_assumable_by_compute_services(self):
"""Determines whether or not the role is assumed from a compute service, and if so which ones."""
# sts:AssumeRole must be there
lowercase_actions = [x.lower() for x in self.actions]
if "sts:AssumeRole".lower() not in lowercase_actions:
return []
assumable_by_compute_services = []
if self.principals:
for principal in self.principals:
if principal.endswith(".amazonaws.com"):
service_prefix_to_evaluate = principal.split(".")[0]
if (
service_prefix_to_evaluate
in SERVICE_PREFIXES_WITH_COMPUTE_ROLES
):
assumable_by_compute_services.append(service_prefix_to_evaluate)
return assumable_by_compute_services
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/authorization_details.py�����������������������������������0000644�0001751�0000164�00000065411�13702127516�026263� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Represents the entire JSON file generated by the aws iam get-account-authorization-details command."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
from operator import itemgetter
from policy_sentry.querying.all import get_all_service_prefixes
# from cloudsplaining.shared.constants import DEFAULT_EXCLUSIONS_CONFIG
from cloudsplaining.scan.policy_detail import PolicyDetails
from cloudsplaining.scan.principal_detail import PrincipalTypeDetails
from cloudsplaining.output.findings import (
Findings,
UserFinding,
GroupFinding,
RoleFinding,
PolicyFinding,
)
# from cloudsplaining.shared.exclusions import is_name_excluded
from cloudsplaining.shared.exclusions import Exclusions, DEFAULT_EXCLUSIONS
all_service_prefixes = get_all_service_prefixes()
logger = logging.getLogger(__name__)
# pylint: disable=too-many-instance-attributes
class AuthorizationDetails:
"""
Represents the entire JSON file generated by the aws iam get-account-authorization-details command.
"""
def __init__(self, auth_json):
self.auth_json = auth_json
self.policies = PolicyDetails(auth_json.get("Policies", None))
self.user_detail_list = PrincipalTypeDetails(
auth_json.get("UserDetailList", None)
)
self.group_detail_list = PrincipalTypeDetails(
auth_json.get("GroupDetailList", None)
)
self.role_detail_list = PrincipalTypeDetails(
auth_json.get("RoleDetailList", None)
)
self._update_group_membership()
self.findings = Findings()
self.customer_managed_policies_in_use = self._customer_managed_policies_in_use()
self.aws_managed_policies_in_use = self._aws_managed_policies_in_use()
def _update_group_membership(self):
"""A hacky approach to ensuring that groups have their list of members, as that is not included
in the initial AWS API call response and we have to calculate it ourselves."""
# Let's make sure the groups know who their members are
# First, skim through the user_detail_list, and compile the dict of groups and their users
groups = {}
for principal in self.user_detail_list.principals:
if principal.principal_type == "User":
if principal.group_member:
logger.debug(f"User {principal.name} is a member of the group(s): {principal.group_member}")
for group in principal.group_member:
if group not in groups:
groups[group] = []
groups[group].append(principal.name)
else:
groups[group].append(principal.name)
# Let's make sure we add the list of group members to their groups
# We do that by skimming through that groups list and then adding them as class attributes to the principal class.
logger.debug(f"_update_group_membership: groups: {groups}")
for principal in self.group_detail_list.principals:
if principal.principal_type == "Group":
for group in groups:
if group.lower() == principal.name.lower():
principal.members.extend(groups[group])
logger.debug(f"_update_group_membership: The group {group} has members: {groups[group]}")
def _aws_managed_policies_in_use(self):
aws_managed_policies = []
for policy in self.policies.policy_details:
if "arn:aws:iam::aws:" in policy.arn:
aws_managed_policies.append(policy.policy_name)
# Policies attached to groups
for principal in self.group_detail_list.principals:
for attached_managed_policy in principal.attached_managed_policies:
if "arn:aws:iam::aws:" in attached_managed_policy.get("PolicyArn"):
aws_managed_policies.append(
attached_managed_policy.get("PolicyName")
)
# Policies attached to users
for principal in self.user_detail_list.principals:
for attached_managed_policy in principal.attached_managed_policies:
if "arn:aws:iam::aws:" in attached_managed_policy.get("PolicyArn"):
aws_managed_policies.append(
attached_managed_policy.get("PolicyName")
)
# Policies attached to roles
for principal in self.role_detail_list.principals:
for attached_managed_policy in principal.attached_managed_policies:
if "arn:aws:iam::aws:" in attached_managed_policy.get("PolicyArn"):
aws_managed_policies.append(
attached_managed_policy.get("PolicyName")
)
aws_managed_policies = list(dict.fromkeys(aws_managed_policies))
return aws_managed_policies
def _customer_managed_policies_in_use(self):
customer_managed_policies = []
for policy in self.policies.policy_details:
if "arn:aws:iam::aws:" not in policy.arn:
customer_managed_policies.append(policy.policy_name)
# Policies attached to groups
for principal in self.group_detail_list.principals:
for attached_managed_policy in principal.attached_managed_policies:
# Skipping coverage here because it would be redundant
if "arn:aws:iam::aws:" not in attached_managed_policy.get(
"PolicyArn"
): # pragma: no cover
customer_managed_policies.append(
attached_managed_policy.get("PolicyName")
)
# Policies attached to users
for principal in self.user_detail_list.principals:
for attached_managed_policy in principal.attached_managed_policies:
# Skipping coverage here because it would be redundant
if "arn:aws:iam::aws:" not in attached_managed_policy.get(
"PolicyArn"
): # pragma: no cover
customer_managed_policies.append(
attached_managed_policy.get("PolicyName")
)
# Policies attached to roles
for principal in self.role_detail_list.principals:
for attached_managed_policy in principal.attached_managed_policies:
# Skipping coverage here because it would be redundant
if "arn:aws:iam::aws:" not in attached_managed_policy.get(
"PolicyArn"
): # pragma: no cover
customer_managed_policies.append(
attached_managed_policy.get("PolicyName")
)
customer_managed_policies = list(dict.fromkeys(customer_managed_policies))
return customer_managed_policies
@property
def groups(self):
"""A list of the group names in the account, according to the account authorization details."""
group_names = []
for principal in self.group_detail_list.principals:
group_names.append(principal.name)
return group_names
@property
def roles(self):
"""A list of the role names in the account, according to the account authorization details."""
role_names = []
for principal in self.role_detail_list.principals:
role_names.append(principal.name)
return role_names
@property
def users(self):
"""A list of the user names in the account, according to the account authorization details."""
user_names = []
for principal in self.user_detail_list.principals:
user_names.append(principal.name)
return user_names
@property
def principals(self):
"""Get a list of PrincipalDetail objects for all principals - Users, Groups, or Roles - in the account."""
all_principals = []
# Users
for principal in self.user_detail_list.principals:
all_principals.append(principal)
# Groups
for principal in self.group_detail_list.principals:
all_principals.append(principal)
# Roles
for principal in self.role_detail_list.principals:
all_principals.append(principal)
return all_principals
@property
def principal_policy_mapping(self):
"""
Returns a mapping of principals vs the policies that they are attached to - either inline or managed.
"""
principal_policy_mapping = []
for principal in self.principals:
# Inline Policies
if principal.inline_principal_policies:
for inline_policy in principal.inline_principal_policies:
if principal.principal_type == "User":
group_membership = principal.group_member
elif principal.principal_type == "Group":
group_membership = principal.members
else:
group_membership = None
entry = dict(
Principal=principal.name,
Type=principal.principal_type,
PolicyType="Inline",
ManagedBy="Customer",
PolicyName=inline_policy.get("PolicyName"),
GroupMembership=group_membership,
)
principal_policy_mapping.append(entry)
# AttachedManagedPolicies
if principal.attached_managed_policies:
for attached_managed_policy in principal.attached_managed_policies:
if "arn:aws:iam::aws:" in attached_managed_policy.get("PolicyArn"):
managed_by = "AWS"
else:
managed_by = "Customer"
if principal.principal_type == "User":
group_membership = principal.group_member
elif principal.principal_type == "Group":
group_membership = principal.members
else:
group_membership = None
entry = dict(
Principal=principal.name,
Type=principal.principal_type,
PolicyType="Managed",
ManagedBy=managed_by,
PolicyName=attached_managed_policy.get("PolicyName"),
GroupMembership=group_membership,
)
principal_policy_mapping.append(entry)
# While users might have inline policies or managed policies,
# their findings will need to reflect their group membership findings as well.
# So we need to run that loop again, finding the data for their groups and adding it.
if principal.principal_type == "User":
group_memberships = principal.group_member
for group_membership in group_memberships:
for some_principal in self.principals:
if (
some_principal.principal_type == "Group"
and some_principal.name == group_membership
):
if some_principal.inline_principal_policies:
for (
inline_policy
) in some_principal.inline_principal_policies:
entry = dict(
Principal=principal.name,
Type=principal.principal_type,
PolicyType="Inline",
ManagedBy="Customer",
PolicyName=inline_policy.get("PolicyName"),
GroupMembership=principal.group_member,
)
principal_policy_mapping.append(entry)
# AttachedManagedPolicies
if some_principal.attached_managed_policies:
for (
attached_managed_policy
) in some_principal.attached_managed_policies:
if (
"arn:aws:iam::aws:"
in attached_managed_policy.get("PolicyArn")
):
managed_by = "AWS"
else:
managed_by = "Customer"
entry = dict(
Principal=principal.name,
Type=principal.principal_type,
PolicyType="Managed",
ManagedBy=managed_by,
PolicyName=attached_managed_policy.get(
"PolicyName"
),
GroupMembership=principal.group_member,
)
principal_policy_mapping.append(entry)
# Sort it
principal_policy_mapping = sorted(
principal_policy_mapping,
key=itemgetter("Type", "Principal", "PolicyType", "PolicyName"),
)
return principal_policy_mapping
def missing_resource_constraints(
self, exclusions=DEFAULT_EXCLUSIONS, modify_only=True
):
"""Scan the account authorization details for missing resource constraints."""
if not isinstance(exclusions, Exclusions):
raise Exception(
"The provided exclusions is not the Exclusions object type. "
"Please use the Exclusions object."
)
self.findings = Findings(exclusions)
print("-----USERS-----")
self.scan_principal_type_details(self.user_detail_list, exclusions, modify_only)
print("-----GROUPS-----")
self.scan_principal_type_details(self.group_detail_list, exclusions, modify_only)
print("-----ROLES-----")
self.scan_principal_type_details(self.role_detail_list, exclusions, modify_only)
print("-----POLICIES-----")
self.findings.principal_policy_mapping = self.principal_policy_mapping
self.scan_policy_details(exclusions, modify_only)
return self.findings.json
def scan_policy_details(self, exclusions=DEFAULT_EXCLUSIONS, modify_only=True):
"""Scan the PolicyDetails block of the account authorization details output."""
if not isinstance(exclusions, Exclusions):
raise Exception(
"The provided exclusions is not the Exclusions object type. "
"Please use the Exclusions object."
)
for policy in self.policies.policy_details:
print(f"Scanning policy: {policy.policy_name}")
actions_missing_resource_constraints = []
if exclusions.is_policy_excluded(
policy.policy_name
) or exclusions.is_policy_excluded(policy.full_policy_path):
print(f"\tExcluded policy name: {policy.policy_name}")
else:
for statement in policy.policy_document.statements:
if modify_only:
if statement.effect == "Allow":
actions_missing_resource_constraints.extend(
statement.missing_resource_constraints_for_modify_actions(
exclusions
)
)
else:
if statement.effect == "Allow":
actions_missing_resource_constraints.extend(
statement.missing_resource_constraints(exclusions)
)
if actions_missing_resource_constraints:
actions_missing_resource_constraints = list(
dict.fromkeys(actions_missing_resource_constraints)
) # remove duplicates
actions_missing_resource_constraints.sort()
policy_finding = PolicyFinding(
policy_name=policy.policy_name,
arn=policy.arn,
actions=actions_missing_resource_constraints,
policy_document=policy.policy_document,
exclusions=exclusions,
)
self.findings.add_policy_finding(policy_finding)
def scan_principal_type_details(
self,
principal_type_detail_list,
exclusions=DEFAULT_EXCLUSIONS,
modify_only=True,
):
"""Scan the UserDetailList, GroupDetailList, or RoleDetailList
blocks of the account authorization details output."""
if not isinstance(exclusions, Exclusions):
raise Exception(
"The provided exclusions is not the Exclusions object type. "
"Please use the Exclusions object."
)
for principal in principal_type_detail_list.principals:
print(f"Scanning {principal.principal_type}: {principal.name}")
for policy in principal.policy_list:
print(f"\tScanning Policy: {policy['PolicyName']}")
if exclusions.is_policy_excluded(policy["PolicyName"]):
pass
elif principal.is_principal_excluded(exclusions):
print(f"\tExcluded principal name: {principal.name}")
else:
policy_document = policy["PolicyDocument"]
actions_missing_resource_constraints = []
for statement in policy_document.statements:
if modify_only:
if statement.effect == "Allow":
actions_missing_resource_constraints.extend(
statement.missing_resource_constraints_for_modify_actions(
exclusions
)
)
else:
if statement.effect == "Allow":
actions_missing_resource_constraints.extend(
statement.missing_resource_constraints(exclusions)
)
if actions_missing_resource_constraints:
if principal.principal_type == "User":
user_finding = UserFinding(
policy_name=policy["PolicyName"],
arn=principal.arn,
actions=actions_missing_resource_constraints,
policy_document=policy["PolicyDocument"],
exclusions=exclusions,
attached_managed_policies=principal.attached_managed_policies,
group_membership=principal.group_member,
)
self.findings.add_user_finding(user_finding)
elif principal.principal_type == "Group":
group_finding = GroupFinding(
policy_name=policy["PolicyName"],
arn=principal.arn,
actions=actions_missing_resource_constraints,
policy_document=policy["PolicyDocument"],
exclusions=exclusions,
members=principal.members,
attached_managed_policies=principal.attached_managed_policies,
)
logger.debug(f"scan_principal_type_details: The Group {principal.name} has the members {principal.members}")
self.findings.add_group_finding(group_finding)
elif principal.principal_type == "Role":
role_finding = RoleFinding(
policy_name=policy["PolicyName"],
arn=principal.arn,
actions=actions_missing_resource_constraints,
policy_document=policy["PolicyDocument"],
exclusions=exclusions,
assume_role_policy_document=principal.assume_role_policy_document,
attached_managed_policies=principal.attached_managed_policies,
)
self.findings.add_role_finding(role_finding)
class PrincipalPolicyMapping:
"""Mapping between the principals and the policies assigned to them"""
def __init__(self):
self.entries = []
def add_with_detail(
self,
principal_name,
principal_type,
policy_type,
managed_by,
policy_name,
comment,
):
"""Add a new entry to the principal policy mapping"""
entry = PrincipalPolicyMappingEntry(
principal_name,
principal_type,
policy_type,
managed_by,
policy_name,
comment,
)
self.entries.append(entry)
def add(self, principal_policy_mapping_entry):
"""Add a new principal policy mapping entry"""
if not isinstance(principal_policy_mapping_entry, PrincipalPolicyMappingEntry):
raise Exception(
"This should be the object type PrincipalPolicyMappingEntry. Please try again"
)
self.entries.append(principal_policy_mapping_entry)
@property
def json(self):
"""Return the JSON representation of the principal policy mapping"""
entries = [x.json for x in self.entries]
principal_policy_mapping = sorted(
entries, key=itemgetter("Type", "Principal", "PolicyType", "PolicyName")
)
return principal_policy_mapping
@property
def users(self):
"""Return the list of users in the account"""
result = []
for entry in self.entries:
if entry.principal_type == "User":
result.append(entry)
return result
@property
def groups(self):
"""Return the list of groups in the account"""
result = []
for entry in self.entries:
if entry.principal_type == "Group":
result.append(entry)
return result
@property
def roles(self):
"""Return the list of roles in the account"""
result = []
for entry in self.entries:
if entry.principal_type == "Role":
result.append(entry)
return result
def get_post_exclusion_principal_policy_mapping(self, exclusions):
"""Given an Exclusions object, return a principal policy mapping after evaluating exclusions."""
if not isinstance(exclusions, Exclusions):
raise Exception(
"The exclusions provided is not an Exclusions type object. "
"Please supply an Exclusions object and try again."
)
filtered_principal_policy_mapping = PrincipalPolicyMapping()
for user_entry in self.users:
# If the user is explicitly mentioned in exclusions, do not add the entry
if not user_entry.principal_name.lower() in exclusions.users:
# If the user's policy is explicitly mentioned in exclusions, do not add the entry
if not user_entry.policy_name.lower() in exclusions.policies:
# If the user is part of a group that is excluded, do not add that entry
if user_entry.comment:
for group_name in user_entry.comment:
if group_name.lower() not in exclusions.groups:
filtered_principal_policy_mapping.add(user_entry)
for group_entry in self.groups:
if not group_entry.principal_name.lower() in exclusions.groups:
if not group_entry.policy_name.lower() in exclusions.policies:
# If we added users in the previous step that belong to this group name, then add the group
# Otherwise, it means that all the users in that group were excluded individually
# And so far, only user entries have been added to this temporary PrincipalPolicyMapping object
non_excluded_groups = []
for user_entry in filtered_principal_policy_mapping.entries:
if user_entry.comment:
for user_group_membership in user_entry.comment:
non_excluded_groups.append(
user_group_membership.lower()
)
# if the group name is in the list of non-excluded groups
if group_entry.principal_name.lower() in non_excluded_groups:
filtered_principal_policy_mapping.add(group_entry)
for role_entry in self.roles:
if not role_entry.principal_name.lower() in exclusions.roles:
if not role_entry.policy_name.lower() in exclusions.policies:
filtered_principal_policy_mapping.add(role_entry)
return filtered_principal_policy_mapping
class PrincipalPolicyMappingEntry:
"""Describes the mapping between Principals and Policies.
We use this for filtering exclusions and outputting tables of the mapping post-exclusions"""
def __init__(
self,
principal_name,
principal_type,
policy_type,
managed_by,
policy_name,
comment,
):
self.principal_name = principal_name
self.principal_type = principal_type
self.policy_type = policy_type
self.managed_by = managed_by
self.policy_name = policy_name
self.comment = comment
@property
def json(self):
"""Return the JSON representation of the Principal Policy mapping"""
entry = dict(
Principal=self.principal_name,
Type=self.principal_type,
PolicyType=self.policy_type,
ManagedBy=self.managed_by,
PolicyName=self.policy_name,
Comment=self.comment,
)
return entry
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/policy_detail.py�������������������������������������������0000644�0001751�0000164�00000006523�13702127516�024476� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Represents the Policies section of the output generated by the aws iam get-account-authorization-details command."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
from policy_sentry.util.arns import get_account_from_arn
from cloudsplaining.scan.policy_document import PolicyDocument
from cloudsplaining.shared.utils import get_full_policy_path
class PolicyDetails:
"""
Holds PolicyDetail objects. This is sourced from the 'Policies' section of the Authz file - whether they are AWS managed or customer managed.
"""
def __init__(self, policy_details):
self.policy_details = []
for policy_detail in policy_details:
self.policy_details.append(PolicyDetail(policy_detail))
# pylint: disable=too-many-instance-attributes
class PolicyDetail:
"""
Contains information about an IAM policy, including the policy document.
https://docs.aws.amazon.com/IAM/latest/APIReference/API_PolicyDetail.html
"""
def __init__(self, policy_detail):
# Store the Raw JSON data from this for safekeeping
self.policy_detail = policy_detail
# Store the attributes per Policy item
self.policy_name = policy_detail.get("PolicyName")
self.policy_id = policy_detail.get("PolicyId")
self.arn = policy_detail.get("Arn")
self.path = policy_detail.get("Path")
self.default_version_id = policy_detail.get("DefaultVersionId")
self.attachment_count = policy_detail.get("AttachmentCount")
self.permissions_boundary_usage_count = policy_detail.get(
"PermissionsBoundaryUsageCount"
)
self.is_attachable = policy_detail.get("IsAttachable")
self.create_date = policy_detail.get("CreateDate")
self.update_date = policy_detail.get("UpdateDate")
# Policy Documents are stored here. Multiple indices though. We will evaluate the one
# with IsDefaultVersion only.
self.policy_version_list = policy_detail.get("PolicyVersionList")
self.policy_document = self._policy_document()
def _policy_document(self):
"""Return the policy document object"""
policy_document = {}
for policy_version in self.policy_version_list:
if policy_version.get("IsDefaultVersion") is True:
policy_document = PolicyDocument(policy_version.get("Document"))
return policy_document
# This will help with the Exclusions mechanism. Get the full path of the policy, including the name.
@property
def full_policy_path(self):
"""Get the full policy path, including /aws-service-role/, if applicable"""
return get_full_policy_path(self.arn)
@property
def managed_by(self): # pragma: no cover
"""Determine whether the policy is AWS-Managed or Customer-managed based on a Policy ARN pattern."""
if "arn:aws:iam::aws:" in self.arn:
return "AWS"
else:
return "Customer"
@property
def account_id(self): # pragma: no cover
"""Return the account ID"""
if "arn:aws:iam::aws:" in self.arn:
return "N/A"
else:
account_id = get_account_from_arn(self.arn)
return account_id
�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/policy_document.py�����������������������������������������0000644�0001751�0000164�00000014230�13702127516�025044� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""PolicyDocument is re-used whenever IAM Policy Documents are found in the output of the
aws iam get-account-authorization-details command."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
from cloudsplaining.scan.statement_detail import StatementDetail
from cloudsplaining.shared.constants import PRIVILEGE_ESCALATION_METHODS
from cloudsplaining.shared.constants import READ_ONLY_DATA_LEAK_ACTIONS
logger = logging.getLogger(__name__)
RED = "\033[1;31m"
RESET = "\033[0;0m"
class PolicyDocument:
"""
Holds the actual AWS IAM Policy document
"""
def __init__(self, policy):
statement_structure = policy.get("Statement", [])
self.policy = policy
self.statements = []
# leaving here but excluding from tests because IAM Policy grammar dictates that it must be a list
if not isinstance(statement_structure, list):
statement_structure = [statement_structure] # pragma: no cover
for statement in statement_structure:
self.statements.append(StatementDetail(statement))
@property
def json(self):
"""Return the Policy in JSON"""
return self.policy
@property
def all_allowed_actions(self):
"""Output all allowed IAM Actions, regardless of resource constraints"""
allowed_actions = []
for statement in self.statements:
if statement.expanded_actions:
allowed_actions.extend(statement.expanded_actions)
allowed_actions = list(dict.fromkeys(allowed_actions))
return allowed_actions
@property
def all_allowed_unrestricted_actions(self):
"""Output all IAM actions that do not practice resource constraints"""
allowed_actions = []
for statement in self.statements:
if not statement.has_resource_constraints:
if statement.expanded_actions:
allowed_actions.extend(statement.expanded_actions)
allowed_actions = list(dict.fromkeys(allowed_actions))
return allowed_actions
@property
def contains_statement_using_not_action(self):
"""If NotAction is used, flag it so the assessor can triage manually"""
not_action_statements = []
for statement in self.statements:
if statement.not_action:
not_action_statements.append(statement.json)
if not statement.has_resource_constraints and statement.effect_allow:
print(
f"{RED}\tNOTE: The policy has Effect=Allow and uses NotAction without any resource "
f"constraints: {statement.json}{RESET}"
)
return not_action_statements
@property
def allows_privilege_escalation(self):
"""
Determines whether or not the policy allows privilege escalation action combinations published by
Rhino Security Labs.
"""
escalations = []
# all_allowed_actions_lowercase = [x.lower() for x in self.all_allowed_actions]
all_allowed_unrestricted_actions_lowercase = [
x.lower() for x in self.all_allowed_unrestricted_actions
]
for key in PRIVILEGE_ESCALATION_METHODS:
if set(PRIVILEGE_ESCALATION_METHODS[key]).issubset(
all_allowed_unrestricted_actions_lowercase
):
# if set(PRIVILEGE_ESCALATION_METHODS[key]).issubset(all_allowed_actions_lowercase):
escalation = {"type": key, "actions": PRIVILEGE_ESCALATION_METHODS[key]}
escalations.append(escalation)
return escalations
@property
def permissions_management_without_constraints(self):
"""Where applicable, returns a list of 'Permissions management' IAM actions in the statement that
do not have resource constraints"""
result = []
for statement in self.statements:
if statement.permissions_management_actions_without_constraints:
result.extend(
statement.permissions_management_actions_without_constraints
)
return result
@property
def write_actions_without_constraints(self):
"""Where applicable, returns a list of 'Write' level IAM actions in the statement that
do not have resource constraints"""
result = []
for statement in self.statements:
if statement.write_actions_without_constraints:
result.extend(statement.write_actions_without_constraints)
return result
@property
def tagging_actions_without_constraints(self):
"""Where applicable, returns a list of 'Tagging' level IAM actions in the statement that
do not have resource constraints"""
result = []
for statement in self.statements:
if statement.tagging_actions_without_constraints:
result.extend(statement.tagging_actions_without_constraints)
return result
def allows_specific_actions_without_constraints(self, specific_actions):
"""Determine whether or not a list of specific IAM Actions are allowed without resource constraints."""
allowed = []
if not isinstance(specific_actions, list):
raise Exception("Please supply a list of actions.")
# Doing this nested for loop so we can get results that use the official CamelCase actions, and
# the results don't fail if given lowercase input.
# this is less efficient but more accurate and the results are pretty :)
for specific_action in specific_actions:
for allowed_action in self.all_allowed_unrestricted_actions:
if specific_action.lower() == allowed_action.lower():
allowed.append(allowed_action)
return allowed
@property
def allows_data_leak_actions(self):
"""If any 'Data leak' actions are allowed without resource constraints, return those actions."""
return self.allows_specific_actions_without_constraints(
READ_ONLY_DATA_LEAK_ACTIONS
)
������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/principal_detail.py����������������������������������������0000644�0001751�0000164�00000017363�13702127516�025164� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Objects abstracting UserDetailList, GroupDetailList, or RoleDetailList sections of the output generated by the
command `aws iam get-account-authorization-details`"""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
from policy_sentry.util.arns import get_account_from_arn, get_resource_path_from_arn
from cloudsplaining.shared.exclusions import is_name_excluded
from cloudsplaining.scan.policy_document import PolicyDocument
from cloudsplaining.scan.assume_role_policy_document import AssumeRolePolicyDocument
from cloudsplaining.shared.exclusions import DEFAULT_EXCLUSIONS
logger = logging.getLogger(__name__)
class PrincipalTypeDetails:
"""This covers UserDetailList, GroupDetailList, or RoleDetailList"""
def __init__(self, principal_type_details):
self.principals = []
for principal_detail in principal_type_details:
self.principals.append(PrincipalDetail(principal_detail))
# pylint: disable=too-many-instance-attributes
class PrincipalDetail:
"""
Holds data for individual Principal Entries from the Authz file
"""
def __init__(self, principal_detail):
self.principal_detail = principal_detail
if "UserName" in principal_detail:
self.principal_type = "User"
elif "GroupName" in principal_detail:
self.principal_type = "Group"
elif "RoleName" in principal_detail:
self.principal_type = "Role"
# self.principal_policy_list = self._inline_principal_policies()
self.policy_list = []
self.path = principal_detail.get("Path", None)
self.arn = principal_detail.get("Arn", None)
self.tags = principal_detail.get("Tags", None)
self.create_date = principal_detail.get("CreateDate", None)
# This will only appear for Roles, not Users or Groups
self.assume_role_policy_document = self._assume_role_policy_document()
# self.assume_role_policy_document = principal_detail.get("AssumeRolePolicyDocument", None)
self.attached_managed_policies = principal_detail.get("AttachedManagedPolicies")
self.group_member = []
self.members = []
self.inline_principal_policies = self._inline_principal_policies()
if self.principal_type == "User":
self.name = principal_detail.get("UserName", None)
self.id = principal_detail.get("UserId", None)
self.group_member = principal_detail.get("GroupList", None)
policy_list = principal_detail.get("UserPolicyList", None)
if policy_list:
logger.debug(f"Adding {self.principal_type}: {self.name}")
for policy in policy_list:
logger.debug(
f"\tAdding {policy.get('PolicyName', None)} which is attached to the {self.principal_type} {self.name}"
)
self.policy_list.append(
{
"PolicyName": policy.get("PolicyName", None),
"PolicyDocument": PolicyDocument(
policy.get("PolicyDocument", None)
),
}
)
elif self.principal_type == "Group":
self.name = principal_detail.get("GroupName", None)
self.id = principal_detail.get("GroupId", None)
policy_list = principal_detail.get("GroupPolicyList", None)
if policy_list:
logger.debug(f"Adding {self.principal_type}: {self.name}")
for policy in policy_list:
logger.debug(
f"\tAdding {policy.get('PolicyName', None)} which is attached to the {self.principal_type} {self.name}"
)
self.policy_list.append(
{
"PolicyName": policy.get("PolicyName", None),
"PolicyDocument": PolicyDocument(
policy.get("PolicyDocument", None)
),
}
)
elif self.principal_type == "Role":
self.name = principal_detail.get("RoleName", None)
self.id = principal_detail.get("RoleId", None)
policy_list = principal_detail.get("RolePolicyList", None)
if policy_list:
logger.debug(f"Adding {self.principal_type}: {self.name}")
for policy in policy_list:
logger.debug(
f"\tAdding {policy.get('PolicyName', None)} which is attached to the {self.principal_type} {self.name}"
)
self.policy_list.append(
{
"PolicyName": policy.get("PolicyName", None),
"PolicyDocument": PolicyDocument(
policy.get("PolicyDocument", None)
),
}
)
def _inline_principal_policies(self):
"""Stores the list of policies attached to the Principal."""
inline_principal_policies = []
if self.principal_type == "User":
inline_principal_policies = self.principal_detail.get(
"UserPolicyList", None
)
if self.principal_type == "Group":
inline_principal_policies = self.principal_detail.get(
"GroupPolicyList", None
)
if self.principal_type == "Role":
inline_principal_policies = self.principal_detail.get(
"RolePolicyList", None
)
return inline_principal_policies
def _assume_role_policy_document(self):
"""Set the assume role policy document"""
if self.principal_type == "Role":
this_document = self.principal_detail.get("AssumeRolePolicyDocument", None)
if this_document:
assume_role_policy_document = AssumeRolePolicyDocument(this_document)
return assume_role_policy_document
# For roles, a trust policy is required. I'm simply including an else statement here
# to make Pylint and coverage happy.
else:
return None # pragma: no cover
else:
return None
@property
def assume_role_from_compute(self): # pragma: no cover
"""Parse the Trust Policy and determine if an AWS Compute service (EC2, ECS, EKS, Lambda)
is able to assume the role."""
if self.principal_type == "Role":
return self.assume_role_policy_document
else:
return None
@property
def account_id(self):
"""Return the account ID"""
account_id = get_account_from_arn(self.arn)
return account_id
def is_principal_excluded(self, exclusions=DEFAULT_EXCLUSIONS):
"""According to the exclusions configuration, determine whether or not to skip the Principal according
to their name."""
decision = False
name = get_resource_path_from_arn(self.arn)
if self.principal_type == "User":
if is_name_excluded(name, exclusions.users):
print(f"\tExcluded user: {name}")
decision = True
if self.principal_type == "Group":
if is_name_excluded(name, exclusions.groups):
print(f"\tExcluded group: {name}")
decision = True
if self.principal_type == "Role":
if is_name_excluded(name, exclusions.roles):
print(f"\tExcluded role: {name}")
decision = True
return decision
�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/scan/statement_detail.py����������������������������������������0000644�0001751�0000164�00000026410�13702127516�025200� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Abstracts evaluation of IAM Policy statements."""
import logging
from policy_sentry.analysis.analyze import determine_actions_to_expand
from policy_sentry.querying.actions import (
remove_actions_not_matching_access_level,
get_actions_matching_arn,
)
from policy_sentry.querying.all import get_all_actions
from cloudsplaining.shared.utils import (
remove_read_level_actions,
remove_wildcard_only_actions,
)
from cloudsplaining.shared.exclusions import DEFAULT_EXCLUSIONS, Exclusions
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
logger = logging.getLogger(__name__)
logging.getLogger("policy_sentry").setLevel(logging.WARNING)
all_actions = get_all_actions()
# pylint: disable=too-many-instance-attributes
class StatementDetail:
"""
Analyzes individual statements within a policy
"""
def __init__(self, statement):
self.json = statement
self.statement = statement
self.effect = statement["Effect"]
self.resources = self._resources()
self.actions = self._actions()
self.not_action = self._not_action()
self.not_action_effective_actions = self._not_action_effective_actions()
self.not_resource = self._not_resource()
def _actions(self):
"""Holds the actions in a statement"""
actions = self.statement.get("Action")
if not actions:
return []
if not isinstance(actions, list):
actions = [actions]
return actions
def _resources(self):
"""Holds the resource ARNs in a statement"""
resources = self.statement.get("Resource")
if not resources:
return []
# If it's a string, turn it into a list
if not isinstance(resources, list):
resources = [resources]
return resources
def _not_action(self):
"""Holds the NotAction details.
We won't do anything with it - but we will flag it as something for the assessor to triage."""
not_action = self.statement.get("NotAction")
if not not_action:
return []
if not isinstance(not_action, list):
not_action = [not_action]
return not_action
def _not_resource(self):
"""Holds the NotResource details.
We won't do anything with it - but we will flag it as something for the assessor to triage."""
not_resource = self.statement.get("NotResource")
if not not_resource:
return []
if not isinstance(not_resource, list):
not_resource = [not_resource]
return not_resource
# @property
def _not_action_effective_actions(self):
"""If NotAction is used, calculate the allowed actions - i.e., what it would be """
effective_actions = []
if not self.not_action:
return None
not_actions_expanded = determine_actions_to_expand(self.not_action)
not_actions_expanded_lowercase = [x.lower() for x in not_actions_expanded]
# Effect: Allow && Resource != "*"
if self.has_resource_constraints and self.effect_allow:
opposite_actions = []
for arn in self.resources:
actions_specific_to_arn = get_actions_matching_arn(arn)
if actions_specific_to_arn:
opposite_actions.extend(get_actions_matching_arn(arn))
for opposite_action in opposite_actions:
# If it's in NotActions, then it is not an action we want
if opposite_action.lower() in not_actions_expanded_lowercase:
pass
# Otherwise add it
else:
effective_actions.append(opposite_action)
effective_actions.sort()
return effective_actions
# Effect: Allow, Resource != "*", and Action == prefix:*
elif not self.has_resource_constraints and self.effect_allow:
# Then we calculate the reverse using all_actions
for action in all_actions:
# If it's in NotActions, then it is not an action we want
if action.lower() in not_actions_expanded_lowercase:
pass
# Otherwise add it
else:
effective_actions.append(action)
effective_actions.sort()
return effective_actions
elif self.has_resource_constraints and self.effect_deny:
logger.debug("NOTE: Haven't decided if we support Effect Deny here?")
return None
elif not self.has_resource_constraints and self.effect_deny:
logger.debug("NOTE: Haven't decided if we support Effect Deny here?")
return None
# only including this so Pylint doesn't yell at us
else:
return None # pragma: no cover
@property
def has_not_resource_with_allow(self):
"""Per the AWS documentation, the NotResource should NEVER be used with the Allow Effect.
See documentation here. https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_policies_elements_notresource.html#notresource-element-combinations"""
result = False
if self.not_resource:
if self.effect_allow:
result = True
logger.warning(
"Per the AWS documentation, the NotResource should never be used with the "
"Allow Effect. We suggest changing this ASAP"
)
return result
@property
def expanded_actions(self):
"""Expands the full list of allowed actions from the Policy/"""
if self.actions:
expanded = determine_actions_to_expand(self.actions)
expanded.sort()
return expanded
elif self.not_action:
return self.not_action_effective_actions
else:
raise Exception( # pragma: no cover
"The Policy should include either NotAction or Action in the statement."
)
@property
def effect_deny(self):
"""Check if the Effect of the Policy is 'Deny'"""
return bool(self.effect == "Deny")
@property
def effect_allow(self):
"""Check if the Effect of the Policy is 'Allow'"""
return bool(self.effect == "Allow")
@property
def services_in_use(self):
"""Get a list of the services in use by the statement."""
service_prefixes = []
for action in self.expanded_actions:
service, action_name = action.split(":") # pylint: disable=unused-variable
if service not in service_prefixes:
service_prefixes.append(service)
service_prefixes.sort()
return service_prefixes
@property
def has_resource_constraints(self):
"""Determine whether or not the statement allows resource constraints."""
answer = True
if len(self.resources) == 0:
# This is probably a NotResources situation which we do not support.
pass
if len(self.resources) == 1:
if self.resources[0] == "*":
answer = False
elif len(self.resources) > 1: # pragma: no cover
# It's possible that someone writes a bad policy that includes both a resource ARN as well as a wildcard.
for resource in self.resources:
if resource == "*":
answer = False
return answer
@property
def permissions_management_actions_without_constraints(self):
"""Where applicable, returns a list of 'Permissions management' IAM actions in the statement that
do not have resource constraints"""
result = []
if not self.has_resource_constraints:
if self.expanded_actions:
result = remove_actions_not_matching_access_level(
self.expanded_actions, "Permissions management"
)
return result
@property
def write_actions_without_constraints(self):
"""Where applicable, returns a list of 'Write' level IAM actions in the statement that
do not have resource constraints"""
result = []
if not self.has_resource_constraints:
result = remove_actions_not_matching_access_level(
self.expanded_actions, "Write"
)
return result
@property
def tagging_actions_without_constraints(self):
"""Where applicable, returns a list of 'Tagging' level IAM actions in the statement that
do not have resource constraints"""
result = []
if not self.has_resource_constraints:
result = remove_actions_not_matching_access_level(
self.expanded_actions, "Tagging"
)
return result
def missing_resource_constraints(self, exclusions=DEFAULT_EXCLUSIONS):
"""Return a list of any actions - regardless of access level - allowed by the statement that do not leverage
resource constraints."""
if not isinstance(exclusions, Exclusions):
raise Exception( # pragma: no cover
"The provided exclusions is not the Exclusions object type. "
"Please use the Exclusions object."
)
actions_missing_resource_constraints = []
if len(self.resources) == 1:
if self.resources[0] == "*":
actions_missing_resource_constraints = remove_wildcard_only_actions(
self.expanded_actions
)
results = exclusions.get_allowed_actions(actions_missing_resource_constraints)
return results
def missing_resource_constraints_for_modify_actions(
self, exclusions=DEFAULT_EXCLUSIONS
):
"""
Determine whether or not any actions at the 'Write', 'Permissions management', or 'Tagging' access levels
are allowed by the statement without resource constraints.
:param exclusions: Exclusions object
"""
if not isinstance(exclusions, Exclusions):
raise Exception( # pragma: no cover
"The provided exclusions is not the Exclusions object type. "
"Please use the Exclusions object."
)
# This initially includes read-only and modify level actions
if exclusions.include_actions is None:
always_look_for_actions = [] # pragma: no cover
else:
always_look_for_actions = exclusions.include_actions
actions_missing_resource_constraints = self.missing_resource_constraints(
exclusions
)
always_actions_found = []
for action in actions_missing_resource_constraints:
if action.lower() in [x.lower() for x in always_look_for_actions]:
always_actions_found.append(action)
modify_actions_missing_constraints = remove_read_level_actions(
actions_missing_resource_constraints
)
modify_actions_missing_constraints = (
modify_actions_missing_constraints + always_actions_found
)
modify_actions_missing_constraints = list(
dict.fromkeys(modify_actions_missing_constraints)
)
modify_actions_missing_constraints.sort()
return modify_actions_missing_constraints
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/shared/���������������������������������������������������������0000755�0001751�0000164�00000000000�13702127551�021616� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/shared/__init__.py����������������������������������������������0000644�0001751�0000164�00000000140�13702127516�023723� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# pylint: disable=missing-module-docstring
import logging
logger = logging.getLogger(__name__)
��������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/shared/constants.py���������������������������������������������0000644�0001751�0000164�00000010467�13702127516�024215� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Some useful variables to import from various parts of this program."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import os
import logging
import yaml
from cloudsplaining.shared.validation import check_exclusions_schema
logger = logging.getLogger(__name__)
PACKAGE_DIR = str(
os.path.abspath(os.path.join(os.path.dirname(__file__), os.path.pardir))
)
EXCLUSIONS_FILE = str(os.path.join(PACKAGE_DIR, "shared", "default-exclusions.yml"))
if EXCLUSIONS_FILE:
with open(EXCLUSIONS_FILE, "r") as yaml_file:
try:
DEFAULT_EXCLUSIONS_CONFIG = yaml.safe_load(yaml_file)
except yaml.YAMLError as exc:
logger.critical(exc)
check_exclusions_schema(DEFAULT_EXCLUSIONS_CONFIG)
EXCLUSIONS_TEMPLATE = """# Policy names to exclude from evaluation
# Suggestion: Add policies here that are known to be overly permissive by design, after you run the initial report.
policies:
- "AWSServiceRoleFor*"
- "*ServiceRolePolicy"
- "*ServiceLinkedRolePolicy"
- "AdministratorAccess" # Otherwise, this will take a long time
- "service-role*"
- "aws-service-role*"
# Don't evaluate these roles, users, or groups as part of the evaluation
roles:
- "service-role*"
- "aws-service-role*"
users:
- ""
groups:
- ""
# Read-only actions to include in the results, such as s3:GetObject
# By default, it includes Actions that could lead to Data Leaks
include-actions:
- "s3:GetObject"
- "ssm:GetParameter"
- "ssm:GetParameters"
- "ssm:GetParametersByPath"
- "secretsmanager:GetSecretValue"
# Write actions to include from the results, such as kms:Decrypt
exclude-actions:
- ""
"""
# These are some high-priority, read-only IAM actions that could lead to a data leak if
# used on certain data storage resources.
# These are not meant to cover every possibility - just high priority ones.
# For now, we have included s3, SSM Parameter Store, and Secrets Manager.
# Feel free to open up a GitHub issue if you have suggestions.
READ_ONLY_DATA_LEAK_ACTIONS = [
"s3:GetObject",
"ssm:GetParameter",
"ssm:GetParameters",
"ssm:GetParametersByPath",
"secretsmanager:GetSecretValue",
]
PRIVILEGE_ESCALATION_METHODS = {
# 1. IAM Permissions on Other Users
"CreateAccessKey": ["iam:createaccesskey"],
"CreateLoginProfile": ["iam:createloginprofile"],
"UpdateLoginProfile": ["iam:updateloginprofile"],
# 2. Permissions on Policies
"CreateNewPolicyVersion": ["iam:createpolicyversion"],
"SetExistingDefaultPolicyVersion": ["iam:setdefaultpolicyversion"],
"AttachUserPolicy": ["iam:attachuserpolicy"],
"AttachGroupPolicy": ["iam:attachgrouppolicy"],
"AttachRolePolicy": ["iam:attachrolepolicy", "sts:assumerole"],
"PutUserPolicy": ["iam:putuserpolicy"],
"PutGroupPolicy": ["iam:putgrouppolicy"],
"PutRolePolicy": ["iam:putrolepolicy", "sts:assumerole"],
"AddUserToGroup": ["iam:addusertogroup"],
# 3. Updating an AssumeRolePolicy
"UpdateRolePolicyToAssumeIt": ["iam:updateassumerolepolicy", "sts:assumerole"],
# 4. iam:PassRole:*
"CreateEC2WithExistingIP": ["iam:passrole", "ec2:runinstances"],
"PassExistingRoleToNewLambdaThenInvoke": [
"iam:passrole",
"lambda:createfunction",
"lambda:invokefunction",
],
"PassExistingRoleToNewLambdaThenTriggerWithNewDynamo": [
"iam:passrole",
"lambda:createfunction",
"lambda:createeventsourcemapping",
"dynamodb:createtable",
"dynamodb:putitem",
],
"PassExistingRoleToNewLambdaThenTriggerWithExistingDynamo": [
"iam:passrole",
"lambda:createfunction",
"lambda:createeventsourcemapping",
],
"PassExistingRoleToNewGlueDevEndpoint": ["iam:passrole", "glue:createdevendpoint",],
"PassExistingRoleToCloudFormation": ["iam:passrole", "cloudformation:createstack",],
"PassExistingRoleToNewDataPipeline": [
"iam:passrole",
"datapipeline:createpipeline",
],
# 5. Privilege Escalation Using AWS Services
"UpdateExistingGlueDevEndpoint": ["glue:updatedevendpoint"],
"EditExistingLambdaFunctionWithRole": ["lambda:updatefunctioncode"],
}
SERVICE_PREFIXES_WITH_COMPUTE_ROLES = ["ec2", "eks", "ecs-tasks", "lambda"]
���������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/shared/default-exclusions.yml�����������������������������������0000644�0001751�0000164�00000001664�13702127516�026167� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# Policy names to exclude from evaluation
# Suggestion: Add policies here that are known to be overly permissive by design, after you run the initial report.
policies:
- "AWSServiceRoleFor*"
- "*ServiceRolePolicy"
- "*ServiceLinkedRolePolicy"
- "AdministratorAccess" # Otherwise, this will take a long time
- "service-role*"
- "aws-service-role*"
- "MyRole"
# Don't evaluate these roles, users, or groups as part of the evaluation
roles:
- "service-role*"
- "aws-service-role*"
users:
- ""
groups:
- ""
# Read-only actions to include in the results, such as s3:GetObject
# By default, it includes Actions that could lead to Data Leaks
include-actions:
- "s3:GetObject"
- "ssm:GetParameter"
- "ssm:GetParameters"
- "ssm:GetParametersByPath"
- "secretsmanager:GetSecretValue"
- "rds:CopyDBSnapshot"
- "rds:CreateDBSnapshot"
# Write actions to include from the results, such as kms:Decrypt
exclude-actions:
- ""
����������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/shared/exclusions.py��������������������������������������������0000644�0001751�0000164�00000015045�13702127516�024372� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Manages the exclusions template for scanning the Authorizations file"""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
from cloudsplaining.shared.validation import check_exclusions_schema
from cloudsplaining.shared.constants import DEFAULT_EXCLUSIONS_CONFIG
logger = logging.getLogger(__name__)
class Exclusions:
"""Contains the exclusions configuration as an object"""
def __init__(self, exclusions_config=DEFAULT_EXCLUSIONS_CONFIG):
check_exclusions_schema(exclusions_config)
self.config = exclusions_config
self.include_actions = self._include_actions()
self.exclude_actions = self._exclude_actions()
self.roles = self._roles()
self.users = self._users()
self.groups = self._groups()
self.policies = self._policies()
def _roles(self):
provided_roles = self.config.get("roles", None)
roles = []
# Normalize for comparisons
if provided_roles:
for role in provided_roles:
roles.append(role.lower())
return roles
def _users(self):
provided_users = self.config.get("users", None)
users = []
if provided_users:
# Normalize for comparisons
for user in provided_users:
users.append(user.lower())
return users
def _groups(self):
provided_groups = self.config.get("groups", None)
groups = []
if provided_groups:
# Normalize for comparisons
for group in provided_groups:
groups.append(group.lower())
return groups
def _policies(self):
provided_policies = self.config.get("policies", None)
policies = []
if provided_policies:
# Normalize for comparisons
for policy in provided_policies:
policies.append(policy.lower())
return policies
def _include_actions(self):
include_actions = self.config.get("include-actions", None)
# Set to lowercase so subsequent evaluations are faster.
if include_actions:
always_include_actions = [x.lower() for x in include_actions]
return always_include_actions
else:
return []
def _exclude_actions(self):
exclude_actions = self.config.get("exclude-actions", None)
if exclude_actions:
always_exclude_actions = [x.lower() for x in exclude_actions]
return always_exclude_actions
else:
return []
def is_action_always_included(self, action_in_question):
"""
Supply an IAM action, and get a decision about whether or not it is excluded.
:return:
"""
if self.include_actions:
if action_in_question.lower() in self.include_actions:
return action_in_question
else:
return False
else:
return False
def is_action_always_excluded(self, action_in_question):
"""
Supply an IAM action, and get a decision about whether or not it is always included.
:return:
"""
if self.exclude_actions:
return bool(
is_name_excluded(action_in_question.lower(), self.exclude_actions)
)
else:
return False # pragma: no cover
def is_policy_excluded(self, policy_name):
"""
Supply a policy name or path, and get a decision about whether or not it is excluded.
:param policy_name: Policy name or Policy path
:return:
"""
return bool(is_name_excluded(policy_name, self.policies))
def is_principal_excluded(self, principal, principal_type):
"""
Supply a principal name or path, and get a decision about whether or not it is excluded.
:param principal: a principal name or path
:param principal_type: User, Group, or Role
:return: a boolean decision
"""
if principal_type == "User":
return bool(is_name_excluded(principal.lower(), self.users))
elif principal_type == "Group":
return bool(is_name_excluded(principal.lower(), self.groups))
elif principal_type == "Role":
return bool(is_name_excluded(principal.lower(), self.roles))
else: # pragma: no cover
raise Exception(
"Please supply User, Group, or Role as the principal argument."
)
def get_allowed_actions(self, requested_actions):
"""Given a list of actions, it will evaluate those actions against the exclusions configuration and return a
list of actions after filtering for exclusions. """
always_include_actions = []
# ALWAYS INCLUDE ACTIONS
for action in requested_actions:
for include_action in self.include_actions:
if action.lower() == include_action.lower():
always_include_actions.append(action)
# RULE OUT EXCLUDED ACTIONS
actions_minus_exclusions = []
for action in requested_actions:
if not is_name_excluded(action.lower(), self.exclude_actions):
actions_minus_exclusions.append(action)
results = always_include_actions + actions_minus_exclusions
results = list(dict.fromkeys(results))
return results
# pylint: disable=inconsistent-return-statements
def is_name_excluded(name, exclusions_list):
"""
:param name: The name of the policy, role, user, or group
:param exclusions_list: List of exclusions
:return:
"""
for exclusion in exclusions_list:
# Skip empty items
if exclusion == "":
continue
if exclusion.lower() == name.lower():
logger.debug(f"\tExcluded: {exclusion}")
return True
# ThePerfectManDoesntExi*
if exclusion.endswith("*"):
prefix = exclusion[: exclusion.index("*")]
# print(prefix)
if name.lower().startswith(prefix.lower()):
# logger.debug(f"Excluded prefix: {exclusion}")
print(f"\tExcluded prefix: {exclusion}")
return True
if exclusion.startswith("*"):
suffix = exclusion.split("*")[-1]
if name.lower().endswith(suffix.lower()):
print(f"\tExcluded suffix: {exclusion}")
return True
DEFAULT_EXCLUSIONS = Exclusions(DEFAULT_EXCLUSIONS_CONFIG)
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/shared/utils.py�������������������������������������������������0000644�0001751�0000164�00000006045�13702127516�023336� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Just some utility functions that don't fit neatly into other categories"""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
from policy_sentry.querying.actions import (
get_action_data,
remove_actions_not_matching_access_level,
)
from policy_sentry.querying.all import get_all_service_prefixes
all_service_prefixes = get_all_service_prefixes()
logger = logging.getLogger(__name__)
def remove_wildcard_only_actions(actions_list):
"""Given a list of actions, remove the ones that CANNOT be restricted to ARNs, leaving only the ones that CAN."""
try:
actions_list_unique = list(dict.fromkeys(actions_list))
except TypeError as t_e: # pragma: no cover
print(t_e)
return []
results = []
for action in actions_list_unique:
service_prefix, action_name = action.split(":")
if service_prefix not in all_service_prefixes:
continue # pragma: no cover
action_data = get_action_data(service_prefix, action_name)
if len(action_data[service_prefix]) == 0:
pass # pragma: no cover
elif len(action_data[service_prefix]) == 1:
if action_data[service_prefix][0]["resource_arn_format"] == "*":
pass
else:
# Let's return the CamelCase action name format
results.append(action_data[service_prefix][0]["action"])
else:
results.append(action_data[service_prefix][0]["action"])
return results
def remove_read_level_actions(actions_list):
"""Given a set of actions, return that list of actions,
but only with actions at the 'Write', 'Tagging', or 'Permissions management' levels"""
write_actions = remove_actions_not_matching_access_level(actions_list, "Write")
permissions_management_actions = remove_actions_not_matching_access_level(
actions_list, "Permissions management"
)
tagging_actions = remove_actions_not_matching_access_level(actions_list, "Tagging")
modify_actions = tagging_actions + write_actions + permissions_management_actions
return modify_actions
def get_full_policy_path(arn):
"""
Resource string will output strings like the following examples.
Case 1:
Input: arn:aws:iam::aws:policy/aws-service-role/AmazonGuardDutyServiceRolePolicy
Output:
aws-service-role/AmazonGuardDutyServiceRolePolicy
Case 2:
Input: arn:aws:iam::123456789012:role/ExampleRole
Output: ExampleRole
:param arn:
:return:
"""
split_arn = arn.split(":")
resource_string = ":".join(split_arn[5:])
resource_string = resource_string.split("/")[1:]
resource_string = "/".join(resource_string)
return resource_string
def capitalize_first_character(some_string):
"""Description: Capitalizes the first character of a string"""
return " ".join("".join([w[0].upper(), w[1:].lower()]) for w in some_string.split())
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining/shared/validation.py��������������������������������������������0000644�0001751�0000164�00000004343�13702127516�024327� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������"""Validate JSON/YAML formatted templates/data, such as the exclusions template and the Authorization details file."""
# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import logging
from schema import Optional, Schema, SchemaError
logger = logging.getLogger(__name__)
EXCLUSIONS_TEMPLATE_SCHEMA = Schema(
{
Optional("policies"): [str],
Optional("roles"): [str],
Optional("users"): [str],
Optional("groups"): [str],
Optional("exclude-actions"): [str],
Optional("include-actions"): [str],
}
)
AUTHORIZATION_DETAILS_SCHEMA = Schema(
{
"UserDetailList": [object],
"GroupDetailList": [object],
"RoleDetailList": [object],
"Policies": [object],
}
)
# pragma: no cover
def check(conf_schema, conf):
"""
Validates a user-supplied JSON vs a defined schema.
:param conf_schema: The Schema object that defines the required structure.
:param conf: The user-supplied schema to validate against the required structure.
"""
try:
conf_schema.validate(conf)
return True
except SchemaError as schema_error:
try:
# workarounds for Schema's logging approach
print(schema_error.autos[0])
detailed_error_message = schema_error.autos[2]
print(detailed_error_message.split(" in {'")[0]) # pragma: no cover
# for error in schema_error.autos:
except: # pylint: disable=bare-except
logger.critical(schema_error)
return False
def check_exclusions_schema(cfg):
"""Determine whether or not the exclusions file meets the required format"""
result = check(EXCLUSIONS_TEMPLATE_SCHEMA, cfg)
if result:
return result
else:
raise Exception(
"The required format of the exclusions template is incorrect. Please try again."
)
def check_authorization_details_schema(cfg):
"""Determine whether or not the file meets the required format of the authorizations file"""
result = check(AUTHORIZATION_DETAILS_SCHEMA, cfg)
return result
���������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/�������������������������������������������������������0000755�0001751�0000164�00000000000�13702127550�022041� 5����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/PKG-INFO�����������������������������������������������0000644�0001751�0000164�00000046274�13702127550�023153� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������Metadata-Version: 2.1
Name: cloudsplaining
Version: 0.1.6
Summary: AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report with a triage worksheet.
Home-page: https://github.com/kmcquade/cloudsplaining
Author: Kinnaird McQuade
Author-email: kinnairdm@gmail.com
License: UNKNOWN
Description: Cloudsplaining
--------------
Cloudsplaining is an AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report.

[](https://cloudsplaining.readthedocs.io/en/latest/?badge=latest)
[](https://gitter.im/cloudsplaining?utm_source=badge&utm_medium=badge&utm_campaign=pr-badge&utm_content=badge)
[](https://pepy.tech/project/cloudsplaining)
* [Example report](https://opensource.salesforce.com/cloudsplaining/)
> 
## Documentation
For full documentation, please visit the [project on ReadTheDocs](https://cloudsplaining.readthedocs.io/en/latest/).
* [Installation](#installation)
* [Cheat sheet](#cheatsheet)
* [Example report](https://opensource.salesforce.com/cloudsplaining/)
## Overview
Cloudsplaining identifies violations of least privilege in AWS IAM policies and generates a pretty HTML report with a triage worksheet. It can scan all the policies in your AWS account or it can scan a single policy file.
It helps to identify IAM actions that do not leverage resource constraints. It also helps prioritize the remediation process by flagging IAM policies that present the following risks to the AWS account in question without restriction:
* Data Exfiltration (`s3:GetObject`, `ssm:GetParameter`, `secretsmanager:GetSecretValue`)
* Infrastructure Modification
* Resource Exposure (the ability to modify resource-based policies)
* Privilege Escalation (based on Rhino Security Labs research)
Cloudsplaining also identifies IAM Roles that can be assumed by AWS Compute Services (such as EC2, ECS, EKS, or Lambda), as they can present greater risk than user-defined roles - especially if the AWS Compute service is on an instance that is directly or indirectly exposed to the internet. Flagging these roles is particularly useful to penetration testers (or attackers) under certain scenarios. For example, if an attacker obtains privileges to execute [ssm:SendCommand](https://docs.aws.amazon.com/systems-manager/latest/APIReference/API_SendCommand.html) and there are privileged EC2 instances with the SSM agent installed, they can effectively have the privileges of those EC2 instances. Remote Code Execution via AWS Systems Manager Agent was already a known escalation/exploitation path, but Cloudsplaining can make the process of identifying theses cases easier. See the [sample report](https://opensource.salesforce.com/cloudsplaining/#executive-summary) for some examples.
You can also specify a custom exclusions file to filter out results that are False Positives for various reasons. For example, User Policies are permissive by design, whereas System roles are generally more restrictive. You might also have exclusions that are specific to your organization's multi-account strategy or AWS application architecture.
## Motivation
[Policy Sentry](https://engineering.salesforce.com/salesforce-cloud-security-automating-least-privilege-in-aws-iam-with-policy-sentry-b04fe457b8dc) revealed to us that it is possible to finally write IAM policies according to least privilege in a scalable manner. Before Policy Sentry was released, it was too easy to find IAM policy documents that lacked resource constraints. Consider the policy below, which allows the IAM principal (a role or user) to run `s3:PutObject` on any S3 bucket in the AWS account:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:PutObject"
],
"Resource": "*"
}
]
}
```
This is bad. Ideally, access should be restricted according to resource ARNs, like so:
```json
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetObject"
],
"Resource": "arn:aws:s3:::my-bucket/*"
}
]
}
```
Policy Sentry [makes it really easy to do this](https://github.com/salesforce/policy_sentry/#policy-sentry). Once Infrastructure as Code developers or AWS Administrators gain familiarity with the tool (which is quite easy to use), we've found that adoption starts very quickly. **However**, if you've been using AWS, there is probably a very large backlog of IAM policies that could use an uplift. If you have hundreds of AWS accounts with dozens of policies in each, how can we lock down those AWS accounts by programmatically identifying the policies that should be fixed?
That's why we wrote Cloudsplaining.
Cloudsplaining identifies violations of least privilege in AWS IAM policies and generates a pretty HTML report with a triage worksheet. It can scan all the policies in your AWS account or it can scan a single policy file.
## Installation
* Homebrew
```bash
brew tap salesforce/cloudsplaining https://github.com/salesforce/cloudsplaining
brew install cloudsplaining
```
* Pip3
```bash
pip3 install --user cloudsplaining
```
* Now you should be able to execute `cloudsplaining` from command line by running `cloudsplaining --help`.
### Scanning an entire AWS Account
#### Downloading Account Authorization Details
We can scan an entire AWS account and generate reports. To do this, we leverage the AWS IAM [get-account-authorization-details](https://docs.aws.amazon.com/cli/latest/reference/iam/get-account-authorization-details.html) API call, which downloads a large JSON file (around 100KB per account) that contains all of the IAM details for the account. This includes data on users, groups, roles, customer-managed policies, and AWS-managed policies.
* You must have AWS credentials configured that can be used by the CLI.
* You must have the privileges to run [iam:GetAccountAuthorizationDetails](https://docs.aws.amazon.com/IAM/latest/APIReference/API_GetAccountAuthorizationDetails.html). The `arn:aws:iam::aws:policy/SecurityAudit` policy includes this, as do many others that allow Read access to the IAM Service.
* To download the account authorization details, ensure you are authenticated to AWS, then run `cloudsplaining`'s `download` command:
```bash
cloudsplaining download
```
* If you prefer to use your `~/.aws/credentials` file instead of environment variables, you can specify the profile name:
```bash
cloudsplaining download --profile myprofile
```
It will download a JSON file in your current directory that contains your account authorization detail information.
#### Create Exclusions file
Cloudsplaining tool does not attempt to understand the context behind everything in your AWS account. It's possible to understand the context behind some of these things programmatically - whether the policy is applied to an instance profile, whether the policy is attached, whether inline IAM policies are in use, and whether or not AWS Managed Policies are in use. **Only you know the context behind the design of your AWS infrastructure and the IAM strategy**.
As such, it's important to eliminate False Positives that are context-dependent. You can do this with an exclusions file. We've included a command that will generate an exclusions file for you so you don't have to remember the required format.
You can create an exclusions template via the following command:
```bash
cloudsplaining create-exclusions-file
```
This will generate a file in your current directory titled `exclusions.yml`.
Now when you run the `scan` command, you can use the exclusions file like this:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
For more information on the structure of the exclusions file, see [Filtering False Positives](#filtering-false-positives)
#### Scanning the Authorization Details file
Now that we've downloaded the account authorization file, we can scan *all* of the AWS IAM policies with `cloudsplaining`.
Run the following command:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
It will create an HTML report like [this](https://opensource.salesforce.com/cloudsplaining/):
> 
It will also create a raw JSON data file:
* `default-iam-results.json`: This contains the raw JSON output of the report. You can use this data file for operating on the scan results for various purposes. For example, you could write a Python script that parses this data and opens up automated JIRA issues or Salesforce Work Items. An example entry is shown below. The full example can be viewed at [examples/output/example-authz-details-results.json](examples/files/iam-results-example.json)
```json
{
"example-authz-details": [
{
"AccountID": "012345678901",
"ManagedBy": "Customer",
"PolicyName": "InsecureUserPolicy",
"Arn": "arn:aws:iam::012345678901:user/userwithlotsofpermissions",
"ActionsCount": 2,
"ServicesCount": 1,
"Actions": [
"s3:PutObject",
"s3:PutObjectAcl"
],
"Services": [
"s3"
]
}
]
}
```
See the [examples/files](examples/files) folder for sample output.
#### Filtering False Positives
Resource constraints are best practice - especially for system roles/instance profiles - but sometimes, these are by design. For example, consider a situation where a custom IAM policy is used on an instance profile for an EC2 instance that provisions Terraform. *In this case, broad permissions are design requirements* - so we don't want to include these in the results.
You can create an exclusions template via the following command:
```bash
cloudsplaining create-exclusions-file
```
This will generate a file in your current directory titled `exclusions.yml`.
The default exclusions file looks like this:
```yaml
# Policy names to exclude from evaluation
# Suggestion: Add policies here that are known to be overly permissive by design, after you run the initial report.
policies:
- "AWSServiceRoleFor*"
- "*ServiceRolePolicy"
- "*ServiceLinkedRolePolicy"
- "AdministratorAccess" # Otherwise, this will take a long time
- "service-role*"
- "aws-service-role*"
# Don't evaluate these roles, users, or groups as part of the evaluation
roles:
- "service-role*"
- "aws-service-role*"
users:
- ""
groups:
- ""
# Read-only actions to include in the results, such as s3:GetObject
# By default, it includes Actions that could lead to Data Leaks
include-actions:
- "s3:GetObject"
- "ssm:GetParameter"
- "ssm:GetParameters"
- "ssm:GetParametersByPath"
- "secretsmanager:GetSecretValue"
# Write actions to include from the results, such as kms:Decrypt
exclude-actions:
- ""
```
* Make any additions or modifications that you want.
* Under `policies`, list the path of policy names that you want to exclude.
* If you want to exclude a role titled `MyRole`, list `MyRole` or `MyR*` in the `roles` list.
* You can follow the same approach for `users` and `groups` list.
Now when you run the `scan` command, you can use the exclusions file like this:
```bash
cloudsplaining scan --exclusions-file exclusions.yml --input examples/files/example.json --output examples/files/
```
### Scanning a single policy
You can also scan a single policy file to identify risks instead of an entire account.
```bash
cloudsplaining scan-policy-file --input examples/policies/explicit-actions.json
```
The output will include a finding description and a list of the IAM actions that do not leverage resource constraints.
The output will resemble the following:
```console
Issue found: Data Exfiltration
Actions: s3:GetObject
Issue found: Resource Exposure
Actions: ecr:DeleteRepositoryPolicy, ecr:SetRepositoryPolicy, s3:BypassGovernanceRetention, s3:DeleteAccessPointPolicy, s3:DeleteBucketPolicy, s3:ObjectOwnerOverrideToBucketOwner, s3:PutAccessPointPolicy, s3:PutAccountPublicAccessBlock, s3:PutBucketAcl, s3:PutBucketPolicy, s3:PutBucketPublicAccessBlock, s3:PutObjectAcl, s3:PutObjectVersionAcl
Issue found: Unrestricted Infrastructure Modification
Actions: ecr:BatchDeleteImage, ecr:CompleteLayerUpload, ecr:CreateRepository, ecr:DeleteLifecyclePolicy, ecr:DeleteRepository, ecr:DeleteRepositoryPolicy, ecr:InitiateLayerUpload, ecr:PutImage, ecr:PutImageScanningConfiguration, ecr:PutImageTagMutability, ecr:PutLifecyclePolicy, ecr:SetRepositoryPolicy, ecr:StartImageScan, ecr:StartLifecyclePolicyPreview, ecr:TagResource, ecr:UntagResource, ecr:UploadLayerPart, s3:AbortMultipartUpload, s3:BypassGovernanceRetention, s3:CreateAccessPoint, s3:CreateBucket, s3:DeleteAccessPoint, s3:DeleteAccessPointPolicy, s3:DeleteBucket, s3:DeleteBucketPolicy, s3:DeleteBucketWebsite, s3:DeleteObject, s3:DeleteObjectTagging, s3:DeleteObjectVersion, s3:DeleteObjectVersionTagging, s3:GetObject, s3:ObjectOwnerOverrideToBucketOwner, s3:PutAccelerateConfiguration, s3:PutAccessPointPolicy, s3:PutAnalyticsConfiguration, s3:PutBucketAcl, s3:PutBucketCORS, s3:PutBucketLogging, s3:PutBucketNotification, s3:PutBucketObjectLockConfiguration, s3:PutBucketPolicy, s3:PutBucketPublicAccessBlock, s3:PutBucketRequestPayment, s3:PutBucketTagging, s3:PutBucketVersioning, s3:PutBucketWebsite, s3:PutEncryptionConfiguration, s3:PutInventoryConfiguration, s3:PutLifecycleConfiguration, s3:PutMetricsConfiguration, s3:PutObject, s3:PutObjectAcl, s3:PutObjectLegalHold, s3:PutObjectRetention, s3:PutObjectTagging, s3:PutObjectVersionAcl, s3:PutObjectVersionTagging, s3:PutReplicationConfiguration, s3:ReplicateDelete, s3:ReplicateObject, s3:ReplicateTags, s3:RestoreObject, s3:UpdateJobPriority, s3:UpdateJobStatus
```
## Cheatsheet
```bash
# Download authorization details
cloudsplaining download
# Download from a specific profile
cloudsplaining download --profile someprofile
# Scan Authorization details
cloudsplaining scan --input default.json
# Scan Authorization details with custom exclusions
cloudsplaining scan --input default.json --exclusions-file exclusions.yml
# Scan Policy Files
cloudsplaining scan-policy-file --input examples/policies/wildcards.json
cloudsplaining scan-policy-file --input examples/policies/wildcards.json --exclusions-file examples/example-exclusions.yml
```
## FAQ
**Will it scan all policies by default?**
No, it will only scan policies that are attached to IAM principals.
**Will the download command download all policy versions?**
Not by default. If you want to do this, specify the `--include-non-default-policy-versions` flag. Note that the `scan` tool does not currently operate on non-default versions.
**I followed the installation instructions but can't execute the program via command line at all. What do I do?**
This is likely an issue with your PATH. Your PATH environment variable is not considering the binary packages installed by `pip3`. On a Mac, you can likely fix this by entering the command below, depending on the versions you have installed. YMMV.
```bash
export PATH=$HOME/Library/Python/3.7/bin/:$PATH
```
**I followed the installation instructions but I am receiving a `ModuleNotFoundError` that says `No module named policy_sentry.analysis.expand`. What should I do?**
Try upgrading to the latest version of Cloudsplaining. This error was fixed in version 0.0.10.
## References
* [Policy Sentry](https://github.com/salesforce/policy_sentry/) by [Kinnaird McQuade](https://twitter.com/kmcquade3) at Salesforce
* [Parliament](https://github.com/duo-labs/parliament/) by [Scott Piper](https://twitter.com/0xdabbad00) at [Summit Route](http://summitroute.com/) and Duo Labs.
* [AWS Privilege Escalation Methods](https://github.com/RhinoSecurityLabs/AWS-IAM-Privilege-Escalation) by [Spencer Gietzen](https://twitter.com/SpenGietz) at Rhino Security Labs
* [Understanding Access Level Summaries within Policy Summaries](https://docs.aws.amazon.com/IAM/latest/UserGuide/access_policies_understand-policy-summary-access-level-summaries.html)
* [Leveraging next-generation blockchain-based AI across multiple service meshes to transparently automate multi-cloud IAM wizardry :mage_man:](http://kmcquade.com/rick.html)
Keywords: aws iam roles policy policies privileges security
Platform: UNKNOWN
Classifier: Programming Language :: Python :: 3
Classifier: License :: OSI Approved :: MIT License
Classifier: Operating System :: OS Independent
Requires-Python: >=3.6
Description-Content-Type: text/markdown
������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/SOURCES.txt��������������������������������������������0000644�0001751�0000164�00000004523�13702127550�023731� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������MANIFEST.in
README.md
setup.cfg
setup.py
cloudsplaining/__init__.py
cloudsplaining.egg-info/PKG-INFO
cloudsplaining.egg-info/SOURCES.txt
cloudsplaining.egg-info/dependency_links.txt
cloudsplaining.egg-info/entry_points.txt
cloudsplaining.egg-info/requires.txt
cloudsplaining.egg-info/top_level.txt
cloudsplaining.egg-info/zip-safe
cloudsplaining/bin/__init__.py
cloudsplaining/bin/cli.py
cloudsplaining/bin/version.py
cloudsplaining/command/__init__.py
cloudsplaining/command/create_exclusions_file.py
cloudsplaining/command/download.py
cloudsplaining/command/expand_policy.py
cloudsplaining/command/scan.py
cloudsplaining/command/scan_policy_file.py
cloudsplaining/output/__init__.py
cloudsplaining/output/data_file.py
cloudsplaining/output/findings.py
cloudsplaining/output/report.py
cloudsplaining/output/triage_worksheet.py
cloudsplaining/output/templates/template.html
cloudsplaining/output/templates/analysis/aws-managed.html
cloudsplaining/output/templates/analysis/customer-managed.html
cloudsplaining/output/templates/analysis/finding-card/details.html
cloudsplaining/output/templates/analysis/finding-card/names.html
cloudsplaining/output/templates/appendix/exclusions.html
cloudsplaining/output/templates/appendix/glossary.html
cloudsplaining/output/templates/appendix/references.html
cloudsplaining/output/templates/guidance/1-overview.md
cloudsplaining/output/templates/guidance/2-triage-guidance.md
cloudsplaining/output/templates/guidance/3-remediation-guidance.md
cloudsplaining/output/templates/guidance/4-validation.md
cloudsplaining/output/templates/guidance/glossary.md
cloudsplaining/output/templates/guidance/guidance.html
cloudsplaining/output/templates/summary/aws-managed.html
cloudsplaining/output/templates/summary/customer-managed.html
cloudsplaining/output/templates/summary/executive-summary.html
cloudsplaining/output/templates/summary/iam-principals.html
cloudsplaining/scan/__init__.py
cloudsplaining/scan/assume_role_policy_document.py
cloudsplaining/scan/authorization_details.py
cloudsplaining/scan/policy_detail.py
cloudsplaining/scan/policy_document.py
cloudsplaining/scan/principal_detail.py
cloudsplaining/scan/statement_detail.py
cloudsplaining/shared/__init__.py
cloudsplaining/shared/constants.py
cloudsplaining/shared/default-exclusions.yml
cloudsplaining/shared/exclusions.py
cloudsplaining/shared/utils.py
cloudsplaining/shared/validation.py�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/dependency_links.txt�����������������������������������0000644�0001751�0000164�00000000001�13702127550�026107� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/entry_points.txt���������������������������������������0000644�0001751�0000164�00000000076�13702127550�025342� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������[console_scripts]
cloudsplaining=cloudsplaining.bin.cli:main
������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/requires.txt�������������������������������������������0000644�0001751�0000164�00000000115�13702127550�024436� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������policy_sentry>=0.8.0.3
click
click_log
schema
boto3
botocore
markdown
jinja2
���������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/top_level.txt������������������������������������������0000644�0001751�0000164�00000000017�13702127550�024571� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining
�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/cloudsplaining.egg-info/zip-safe�����������������������������������������������0000644�0001751�0000164�00000000001�13702127550�023471� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������
�������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/setup.cfg����������������������������������������������������������������������0000644�0001751�0000164�00000001305�13702127551�017155� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������[nosetests]
exe = True
tests = test/, test/command/, test/scanning, test/output, test/shared
verbosity = 2
[tool:pytest]
testpaths = test test/command test/scanning test/output test/shared
verbosity = 2
python_files = test/*/test_*.py
ignore = __pycache__ *.pyc
norecursedirs = .svn _build tmp* __pycache__
[coverage:run]
omit =
*/.local/*
utils/*
*/virtualenv/*
*/venv/*
*/.venv/*
cloudsplaining/command/download.py
cloudsplaining/shared/constants.py
cloudsplaining/command/expand_policy.py
cloudsplaining/command/create_exclusions_file.py
cloudsplaining/output/data_file.py
cloudsplaining/output/html_report.py
cloudsplaining/output/triage_worksheet.py
[egg_info]
tag_build =
tag_date = 0
���������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������cloudsplaining-0.1.6/setup.py�����������������������������������������������������������������������0000644�0001751�0000164�00000003705�13702127516�017055� 0����������������������������������������������������������������������������������������������������ustar �runner��������������������������docker��������������������������0000000�0000000������������������������������������������������������������������������������������������������������������������������������������������������������������������������# Copyright (c) 2020, salesforce.com, inc.
# All rights reserved.
# Licensed under the BSD 3-Clause license.
# For full license text, see the LICENSE file in the repo root
# or https://opensource.org/licenses/BSD-3-Clause
import setuptools
import os
import re
HERE = os.path.abspath(os.path.dirname(__file__))
VERSION_RE = re.compile(r'''__version__ = ['"]([0-9.]+)['"]''')
TESTS_REQUIRE = [
'coverage',
'nose',
'pytest'
]
def get_version():
init = open(
os.path.join(
HERE,
"cloudsplaining",
"bin",
'version.py'
)
).read()
return VERSION_RE.search(init).group(1)
def get_description():
return open(
os.path.join(os.path.abspath(HERE), "README.md"), encoding="utf-8"
).read()
setuptools.setup(
name="cloudsplaining",
include_package_data=True,
version=get_version(),
author="Kinnaird McQuade",
author_email="kinnairdm@gmail.com",
description="AWS IAM Security Assessment tool that identifies violations of least privilege and generates a risk-prioritized HTML report with a triage worksheet.",
long_description=get_description(),
long_description_content_type="text/markdown",
url="https://github.com/kmcquade/cloudsplaining",
packages=setuptools.find_packages(exclude=['test*', 'tmp*']),
tests_require=TESTS_REQUIRE,
install_requires=[
'policy_sentry>=0.8.0.3',
'click',
'click_log',
'schema',
'boto3',
'botocore',
'markdown',
'jinja2',
],
classifiers=[
"Programming Language :: Python :: 3",
"License :: OSI Approved :: MIT License",
"Operating System :: OS Independent",
],
entry_points={"console_scripts": "cloudsplaining=cloudsplaining.bin.cli:main"},
zip_safe=True,
keywords='aws iam roles policy policies privileges security',
python_requires='>=3.6',
# scripts=['cloudsplaining/bin/cloudsplaining'],
)
�����������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������������